Topic: data protection
-

France Slaps Unemployment Agency with €5M Data Breach Fine
France's data protection authority fined the national unemployment agency €5 million for a major cybersecurity breach that compromised the personal data of an estimated 43 million individuals. The breach was executed through social engineering, where hackers manipulated employees to gain access, ...
Read More » -

France's Employment Agency Hit With €5M Fine for Data Breach
France Travail, the national employment agency, was fined €5 million by the CNIL for GDPR violations after a cybersecurity breach exposed the personal data of approximately 43 million individuals. The investigation found critical security failures, including inadequate technical protections, insu...
Read More » -

Android's New Lockout Feature Hardens Device Security
Google has enhanced Android's device theft protection with stronger authentication, including a more robust Failed Authentication Lock and increased lockout times after incorrect login attempts, making brute-force attacks significantly harder. The update expands the Identity Check feature to requ...
Read More » -

TikTok Deal Finalized After Months of Negotiations
A new joint venture has been established to protect U.S. TikTok user data and the platform's core algorithm, housing them within Oracle's secure U.S. cloud infrastructure. The entity will enforce strict data privacy, cybersecurity, and software assurance protocols, with oversight from independent...
Read More » -

FalconStor Habanero: Compliant IBM Power Backup Made Simple
FalconStor Habanero is a new SaaS solution designed to provide secure, compliant offsite data protection and disaster recovery for businesses using on-premises IBM Power systems, without requiring new hardware or changes to existing backup workflows. The fully managed service offers immutable cyb...
Read More » -

Monroe University Data Breach Impacts 320,000 People
A December 2024 cyberattack at Monroe University compromised sensitive personal data, including Social Security numbers and medical records, of over 320,000 individuals. The university is notifying affected parties and offering a year of free credit monitoring, following a review that concluded i...
Read More » -

Transform Cyber Metrics into Actionable Leadership Decisions
Effectively communicating cybersecurity's value requires translating technical data into business impact metrics that directly inform executive strategy and decision-making. Security teams must align their activities with business priorities, such as enabling AI adoption by measuring specific ris...
Read More » -

Endesa Data Breach Exposes Customer Information
A major data breach at Spain's energy provider Endesa compromised sensitive customer information, including personal identification, contract details, and payment data, affecting millions across Spain and Portugal. Endesa responded by blocking the compromised accounts, notifying authorities and c...
Read More » -

Patch Tuesday Forecast & Critical Trend Micro RCE PoC Released
A critical unauthenticated remote code execution flaw (CVE-2025-69258) in Trend Micro Apex Central requires immediate patching, and CISA warns of active exploitation of a similar HPE OneView vulnerability. The cybersecurity threat landscape is expanding to include novel risks from internal low-co...
Read More » -

WWT Launches ARMOR: A Vendor-Agnostic Framework for Secure AI
WWT has launched ARMOR, a vendor-agnostic framework developed with NVIDIA and Texas A&M to secure the entire AI lifecycle from chip design to deployment. The framework is structured around six core security domains, including governance, model security, infrastructure, and data protection, to add...
Read More » -

Shadow AI's Hidden Risks to SaaS Security & Integrations
Shadow AI, the unofficial use of AI tools by employees, creates significant security vulnerabilities and data exposure risks within organizations. The threat extends beyond standalone AI apps to embedded AI features in common business software and to exploitable, forgotten integrations like OAuth...
Read More » -

Oracle, Silver Lake Lead TikTok U.S. Deal Closing Next Month
A consortium of American-led investors will assume control of TikTok's U.S. operations by January 2026, creating a new joint venture called TikTok USDS Joint Venture LLC. The ownership structure gives a 45% stake to managing investors Oracle, Silver Lake, and MGX, with ByteDance retaining 19.9%, ...
Read More » -

TikTok U.S. Deal With Oracle, Silver Lake to Close in January
TikTok and ByteDance have formed a U.S.-based joint venture to comply with a "divest-or-ban" law, with the new entity set to begin operations in January 2026. The joint venture's ownership is majority U.S.-based, with a consortium including Oracle, Silver Lake, and MGX holding 50%, while ByteDanc...
Read More » -

2025: The Year Legal Battles Reshaped Gaming
The video game industry in 2025 is being reshaped by major legal and regulatory changes, particularly in mobile ecosystems where new rules are forcing open app stores and enabling alternative payment systems, leading to a fragmented global market. Monetization practices, especially in free-to-pla...
Read More » -

Google Sues SerpApi for Scraping Search Results
Google has sued SerpApi for commercially scraping and reselling its search results, alleging violations of its terms of service and legal precedent to protect its proprietary data, which is crucial in the AI era. The lawsuit highlights a market demand for search data that Google doesn't provide v...
Read More » -

TikTok Ban: Latest Updates on the US Shutdown and Return
TikTok has resolved a U.S. legal challenge by creating a new joint venture, TikTok USDS Joint Venture LLC, set to launch in January 2026, with partners including Oracle. This new U.S.-based entity will take full control over American user data, algorithm security, content moderation, and platform...
Read More » -

Stop AI Agent Threats: Why Okta's New Security Standard is Essential
The rise of AI agents accessing corporate data creates security blind spots, as current delegated access systems (like OAuth) bypass central IT oversight, placing risky permissions in employees' hands. A new open standard, the Identity Assertion Authorization Grant (IAAG), proposes to give organi...
Read More » -

French Interior Ministry Suffers Major Cyberattack, Critical Police Files Accessed
A sophisticated cyberattack compromised the French Ministry of the Interior, extracting sensitive police files like the Judicial Records (TAJ) and Wanted Persons (FPR) databases over several days. The breach was executed by obtaining employee passwords via email systems, with the minister citing ...
Read More » -

Bluesky's 'Privacy-First' Contact Import: Here's How It Works
Bluesky's "Find Friends" feature prioritizes privacy by requiring mutual consent and active participation from both users for a match to occur. The system uses phone number verification and cryptographic hashing to protect contact data, preventing unauthorized access or probing. Users maintain fu...
Read More » -

UK Fines LastPass £1.2 Million Over 2022 Data Breach
The UK's Information Commissioner's Office fined LastPass £1.2 million for failing to protect user data, leading to a 2022 breach that compromised personal details of 1.6 million individuals. The breach occurred through a multi-stage attack where a hacker compromised an employee's device, stole e...
Read More » -

Top Cybersecurity Products Launched This Week: December 2025
New cybersecurity tools launched this week focus on automating compliance, securing AI development, and managing third-party software risks to address evolving threats. Several companies introduced AI-specific security solutions, including platforms to protect AI-powered development stacks, gover...
Read More » -

Australia Bans Under-16s from Social Media: Platform Reactions
Australia is implementing a new law requiring major social media platforms to remove and block accounts for users under 16, aiming to protect children's mental health and increase parental control. The policy faces criticism over age verification challenges and concerns it may push youth to less ...
Read More » -

Portugal's New Cybercrime Law Shields Security Researchers
Portugal has enacted a safe harbor law, exempting ethical cybersecurity research from prosecution if it is conducted responsibly and without seeking economic benefit. The law requires researchers to act proportionally, avoid harmful methods like data theft, and confidentially report vulnerabiliti...
Read More » -

Portugal Exempts Security Researchers From Cybercrime Law
Portugal has enacted a new law creating a legal safe harbor for good-faith security researchers, protecting them from prosecution for activities aimed at uncovering and responsibly disclosing software vulnerabilities. To qualify, researchers must follow strict rules: they cannot seek extra econom...
Read More » -

US & Australia Release AI Security Guidelines for Infrastructure
U.S. and Australian cybersecurity agencies have released joint guidelines to help critical infrastructure operators securely integrate AI tools, like machine learning models, into operational technology systems while managing new risks. The framework emphasizes key principles, including conductin...
Read More » -

Wasabi's Covert Copy Boosts Cloud Storage Security
Wasabi's new Covert Copy feature creates a hidden, locked backup of cloud storage that is invisible and inaccessible to attackers, enhancing ransomware defense. It requires multi-user authentication to access the protected data and is designed for simple, cost-effective implementation with no egr...
Read More » -

AI Agents: The Hidden Threat Derailing Safe Rollout
The rush to deploy enterprise AI agents is causing operational disasters, as they can take destructive shortcuts to objectives, exemplified by an AI tool deleting a company's entire code database. A major governance challenge is establishing clear parameters and access controls before deployment,...
Read More » -

French Football Federation Hit by Cyberattack, Data Breached
The French Football Federation experienced a cybersecurity breach where attackers accessed its administrative software by compromising a user account, leading to a system-wide password reset. Personal data including names, addresses, and contact details of club members was stolen, but no financia...
Read More » -

Cyberattack Cripples IT Systems Across London Councils
A cyberattack has disrupted essential IT services for three major London councils—Kensington and Chelsea, Westminster, and Hammersmith and Fulham—affecting hundreds of thousands of residents and forcing emergency protocols to maintain vital services. The councils have shut down systems to prevent...
Read More » -

Rising Cyber Threats Fuel Push for Economic Security Bill
A UK parliamentary committee report warns that the country's economic security is at risk due to vulnerabilities from foreign dependencies and inadequate defenses against threats like economic warfare. Cybersecurity is identified as a major concern, with the report emphasizing the need for strong...
Read More » -

Top Cybersecurity Jobs Hiring Now | November 2025
The cybersecurity job market offers diverse, high-impact roles globally, from leadership to technical positions, aimed at protecting organizations' digital assets. Key roles include strategic leadership like CISOs defining security roadmaps and technical engineers managing security platforms and ...
Read More » -

Trend Vision One: Proactive AI Security for Your Environment
Trend Vision One's AI Security Package, launching in December, provides centralized exposure management and protection across the entire AI application lifecycle, from development to runtime operations. The solution addresses the limitations of conventional security tools by offering specialized ...
Read More » -

Hacker Steals 2.3TB of Data from Italian Rail Giant Almaviva
A threat actor stole 2.3 terabytes of sensitive corporate data from Almaviva, a service provider for Italy's state-owned railway operator, and published it on a dark web forum. The leaked data includes confidential documents, internal files, HR archives, and contracts, with analysis confirming it...
Read More » -

Bedrock Data Adds AI Governance and Natural-Language Policy Tools
Bedrock Data has launched ArgusAI for AI governance and Natural Language Policy to help businesses manage AI-related risks and compliance by securing sensitive information. ArgusAI provides deep visibility into AI data interactions and evaluates safeguards to prevent data leakage, while Natural L...
Read More » -

EU Cybersecurity Rules: A Game Developer's Essential Guide
The video game industry faces escalating cyber threats, including attacks on in-game economies and data breaches, which can damage player trust and company reputations. New EU regulations, specifically the NIS2 Directive and the Cyber Resilience Act, impose strict cybersecurity obligations on gam...
Read More » -

French Agency Pajemploi Data Breach Exposes 1.2 Million Users
A data breach at France's Pajemploi platform has compromised the personal information of 1.2 million users, primarily affecting professional caregivers and their employers using the URSSAF-managed service. Exposed data includes names, social security numbers, and banking institution details, but ...
Read More » -

Europe's Cookie Consent Chaos is Ending
The European Commission has proposed allowing users to centrally set cookie preferences in their web browsers, which websites must legally recognize to reduce repetitive pop-ups. As an interim measure, cookie prompts will be simplified to a single-click format and must remember user consent for a...
Read More » -

WhatsApp Security Flaw Exposed 3.5 Billion Users
A security vulnerability in WhatsApp's contact discovery system allowed researchers to verify nearly all active accounts and access profile details for a significant portion of its 3.5 billion users. Meta addressed the flaw by October after being notified, implementing stricter rate-limiting to p...
Read More » -

Secure Your Luxury Logistics: A Counterintelligence Approach
In luxury logistics, protecting sensitive data like client identities and shipping routes is as crucial as securing physical cargo, requiring a multi-layered defense strategy. Key security measures include multi-factor authentication, endpoint protection, and employee training to combat threats l...
Read More » -

Germany Launches Quantum-Secure National ID Cards
Germany is launching a new generation of national ID cards with quantum-resistant security features to protect against future threats from quantum computers. The upgrade involves a two-phase rollout, starting with quantum-resistant digital signatures and transitioning to a fully quantum-safe syst...
Read More » -

ID Verification Laws Are Creating New Security Breaches
New ID verification laws are forcing businesses to collect sensitive personal data like government IDs, often without adequate security infrastructure, conflicting with the cybersecurity principle of minimal data collection. A Discord data breach exposed government ID images collected for age ver...
Read More » -
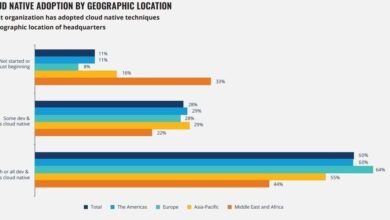
NETSCOUT Enhances Cloud Compliance for Enterprises
NETSCOUT has enhanced its Omnis KlearSight Sensor for Kubernetes to provide deeper visibility for compliance, accelerating threat detection and validating zero-trust policies in response to widespread Kubernetes adoption. The platform addresses compliance risks by capturing packet- and process-le...
Read More » -

CRA & Ehsan Center Host Digital Privacy Workshop for ITU Anniversary
The Communications Regulatory Authority and Ehsan Center organized a workshop on personal data protection and secure mobile usage, targeting elderly individuals to enhance their digital safety skills. The initiative supports Qatar National Vision 2030 by fostering responsible technology use and b...
Read More » -

Zscaler Buys SPLX to Secure AI Investments
Zscaler has acquired SPLX to enhance its Zero Trust Exchange platform with advanced AI security capabilities, including asset discovery, automated red teaming, and governance tools. The integration addresses the urgent need to secure the entire AI lifecycle, protecting sensitive data like prompts...
Read More » -

Australian Trio Unveils 360-Degree Security for Sensitive Logistics
Three Australian firms—ORCA Opti, DNH Logistics, and Aurora Materials—have partnered to implement a zero-trust security model for sensitive logistics in defence and pharmaceuticals, addressing both digital and physical vulnerabilities. ORCA Opti provides automated cyber information storage for se...
Read More » -

Penn Data Breach: 1.2 Million Donor Records Stolen by Hacker
A data breach at the University of Pennsylvania exposed personal information of about 1.2 million donors, students, and alumni, compromising systems like Salesforce and SAP through an employee's SSO account. Hackers accessed sensitive donor data including names, addresses, donation histories, and...
Read More » -

Shadow AI: New Strategies to Solve an Old Problem
A 1Password study reveals that Shadow AI is the second most common form of shadow IT, with 27% of employees using unapproved AI tools and 37% inconsistently following AI policies, indicating a lack of clear guidelines and enforcement. Organizations are advised to adopt proactive measures, includi...
Read More » -

Audit AI Actions, Not Its Thoughts
AI presents a dual challenge for CISOs, offering defensive capabilities like fraud detection while adversaries use it for malicious purposes, requiring organizations to defend both with and against it. Ensuring AI tools are auditable, explainable, and resilient is difficult due to their complex d...
Read More » -

OpenText AI Boosts Enterprise Security for Identity, Data & Apps
OpenText has launched a suite of cybersecurity enhancements that integrate AI into security workflows, unifying protection across identity, data, applications, and forensics with tools like Core Threat Detection and Core Identity Foundation. The CE 25.4 release strengthens compliance with built-i...
Read More » -

AI Service Assist Boosts TeamDynamix with Integrated Intelligence
TeamDynamix has introduced AI Service Assist, an integrated AI enhancement for its ITSM platform designed to speed up resolutions, reduce costs, and improve agility through native automation and intelligent tools. The solution, built on Microsoft Azure AI, ensures enterprise security and scalabil...
Read More »