Topic: cloud security
-

Upwind Raises $250M to Secure AI Workloads in the Cloud
Upwind secured a $250 million Series B investment, bringing its total funding to $430 million to accelerate its runtime-first cloud security platform for AI-driven workloads. The company is experiencing explosive growth, with 900% year-over-year revenue increase and a platform that significantly ...
Read More » -

Upwind Secures $250M at $1.5B Valuation for Cloud Security Platform
Upwind Security has achieved a $1.5 billion valuation after securing $250 million in Series B funding, driven by significant revenue growth and a client base that includes major companies like Siemens and Peloton. The company's core innovation is an "inside-out" runtime security model, which uses...
Read More » -

Concentric AI Launches Private Scan Manager for AWS GovCloud
Concentric AI has expanded its platform to support **AWS GovCloud (US)**, enabling U.S. government agencies and contractors to deploy its AI-driven data security within isolated cloud environments to meet stringent federal compliance standards. The new Private Scan Manager allows these organizati...
Read More » -

MFA Bypass Leads to Major Infostealer Attack on 50 Firms
A major data breach affecting around 50 global companies was enabled by the lack of multi-factor authentication (MFA), allowing an attacker to use stolen credentials for cloud file-sharing platforms. The attacker, using credentials harvested by infostealer malware, accessed accounts where passwor...
Read More » -

Gen AI Data Breaches Surge Over 100%
The enterprise security landscape is being reshaped by generative AI and cloud adoption, forcing a re-evaluation of controls to monitor data flows across unsanctioned personal applications and AI tools. Phishing remains a top threat for credential theft, increasingly targeting cloud logins, while...
Read More » -

Cloud Security Is Lagging Behind
The rapid adoption of cloud technologies has created a significant security gap, with development velocity outpacing protective controls and leaving systems vulnerable to sophisticated, fast-moving attacks. Complex multicloud environments and accelerated software deployment, including AI-generate...
Read More » -

$3.2M Awarded for 11 Zero-Day Cloud Vulnerabilities
The inaugural Zeroday Cloud cybersecurity competition awarded over $300,000 for the discovery of 11 zero-day vulnerabilities in major cloud platforms, highlighting persistent security challenges in complex cloud environments. A critical container escape flaw in the Linux kernel was uncovered, pos...
Read More » -

Astra's Offensive-Grade Scanner Cuts Noise, Proves Risk
Traditional quarterly cloud security scans are insufficient for rapidly changing environments, leading to undetected critical misconfigurations that are a primary cause of breaches. A new scanner addresses this by using an offensive-grade validation engine to actively test and confirm exploitable...
Read More » -

Upwind Integrates Real-Time AI Security into CNAPP Platform
Upwind has integrated a real-time AI security suite into its CNAPP, moving beyond siloed AI security to provide unified, runtime-first protection for AI workloads within the broader cloud ecosystem. The platform addresses modern AI security challenges by offering key functionalities like posture ...
Read More » -

Upwind Launches AI-Powered Exposure Validation Engine for Dynamic CSPM
Upwind's Exposure Validation Engine introduces real-time, dynamic validation for CSPM, moving beyond static checks to confirm live cloud exposures under actual operating conditions. The AI-based framework combines configuration analysis with live reachability testing, simulating attacker methods ...
Read More » -

Corelight's AWS Flow Monitoring Ends Cloud Blind Spots
Corelight's new Flow Monitoring solution for AWS provides unified network visibility across cloud and hybrid infrastructures, reducing SIEM and storage costs by up to 90% compared to traditional methods. The solution converts high-volume AWS flow data into enriched, security-focused intelligence,...
Read More » -

Genetec Adds Audio to Security Centre SaaS
Genetec Inc. has integrated cloud-native audio communications into its Security Centre SaaS platform, enhancing real-time voice capabilities alongside existing video surveillance, access control, and intrusion monitoring in a unified system. This integration allows security teams to verify identi...
Read More » -

Navigating Cloud Complexity for Cyber Resilience
Cloud-first strategies now dominate enterprise infrastructure, with 85% of business applications projected to be SaaS-based, driven by IoT data growth and rapid AI adoption requiring immense processing and storage. The shift to cloud introduces significant security and management challenges, incl...
Read More » -

Microsoft's Entra ID Flaws: A Near-Catastrophic Security Risk
Security researcher Dirk-jan Mollema discovered two severe vulnerabilities in Microsoft’s Entra ID that could have allowed attackers to gain global administrator privileges across nearly all Azure customer environments. The flaws enabled an attacker to impersonate any user in any tenant, potentia...
Read More » -

Microsoft Entra ID Flaw: The Critical Security Risk You Can't Ignore
Security researcher Dirk-jan Mollema discovered two critical vulnerabilities in Microsoft Entra ID that could allow attackers to gain global administrator privileges across nearly all customer tenants. The flaws, involving legacy components like the Access Control Service and Azure Active Directo...
Read More » -

Google Transforms Cloud Security with $32B Wiz Acquisition
Google's $32B acquisition of Wiz marks a significant milestone in enhancing its cloud security capabilities. Discover the strategic implications and future prospects of this groundbreaking move.
Read More » -

Upwind Choppy AI: Simplify Cloud Security Exploration
Upwind has integrated its new Choppy AI into its CNAPP platform, allowing security teams to use natural language to explore and analyze cloud environments while emphasizing transparency and user control. The AI tool translates plain-language questions into visible, editable logic for tasks like i...
Read More » -

Tenable Achieves PROTECTED IRAP & Hits Record Patch Tuesday
Tenable Cloud Security has achieved PROTECTED level certification under Australia's IRAP, validating its robust security controls for government cloud deployments and enabling informed risk-based decisions. The platform addresses multi-cloud security challenges by integrating security throughout ...
Read More » -

Check Point and Wiz Partner to Unify CNAPP and Cloud Security
Check Point and Wiz have launched an integrated cloud security platform that combines prevention-first network security with CNAPP capabilities, enhancing visibility and AI-driven threat prevention. The partnership enables organizations to shift from remediation to prevention, offering real-time ...
Read More » -

Check Point Launches Australian Data Centers for SASE & WAF
Check Point has launched local Australian data centers for its Harmony SASE and CloudGuard WAF services to provide low-latency performance and ensure compliance with national data residency and privacy laws. The new infrastructure helps businesses meet Australian regulations like the SOCI Act and...
Read More » -

Google Drive now blocks ransomware with AI
Google has introduced a new AI-powered feature in Google Drive for desktop that detects ransomware attacks and helps users recover compromised files with minimal effort. The tool automatically halts file synchronization upon detecting suspicious activity, preventing data encryption and allowing q...
Read More » -

Secure Your Google Workspace: Protect Data, Not Just Access
Modern digital workplaces face security challenges from interconnected tools, where attackers exploit legitimate access tokens rather than breaching traditional perimeters. Recent incidents, like the Drift Email compromise, show that third-party integrations can bypass robust security frameworks,...
Read More » -

Rubrik Launches Security Cloud Sovereign for Data Compliance
Rubrik has launched a new solution, Security Cloud Sovereign, to help global organizations meet strict data compliance and security challenges, particularly around data residency and access control. The platform gives customers definitive control over where their data is stored and who can access...
Read More » -

WatchGuard Firewalls Hacked, Fake PoCs Target Security Pros
Critical vulnerabilities in widely used firewalls like WatchGuard are being actively exploited, requiring immediate patching to prevent network breaches. Threat actors are deploying sophisticated social engineering, such as malware disguised as exploit code, and leveraging darknet AI assistants t...
Read More » -

Trend Vision One: Proactive AI Security for Your Environment
Trend Vision One's AI Security Package, launching in December, provides centralized exposure management and protection across the entire AI application lifecycle, from development to runtime operations. The solution addresses the limitations of conventional security tools by offering specialized ...
Read More » -

Hijacked OAuth Apps: Your Cloud's Secret Backdoor
Cybercriminals exploit internal OAuth applications to create persistent backdoors in corporate cloud systems, bypassing security measures like password resets and multi-factor authentication. Attackers deceive users into approving malicious OAuth apps or compromise admin accounts to create truste...
Read More » -

Datadog Secures IRAP Protected Status in Australia
Datadog has achieved IRAP Protected status in Australia, certifying its compliance with stringent security standards for handling sensitive workloads in the public sector and regulated industries. The certification covers Datadog's full suite of observability and security tools, including Infrast...
Read More » -

Securing AI for Space Exploration
Satellite cybersecurity is a growing challenge due to expanding commercial constellations and reliance on delay-prone communication links, creating multiple vulnerabilities. Artificial intelligence is being explored to automate threat detection and response, with debates focusing on centralized, ...
Read More » -

SaaS Security: A New Framework for Essential Controls
Modern enterprises face significant challenges securing their diverse SaaS portfolios due to fragmented security settings and inadequate traditional vendor assessments. The Cloud Security Alliance introduced the SaaS Security Capability Framework (SSCF) to standardize security controls, enabling ...
Read More » -

Indian Bank Data Breach Exposes Thousands of Transfer Records
A significant data breach exposed 273,000 sensitive bank transfer documents from an unsecured Amazon S3 server, compromising account numbers, transaction details, and personal information linked to India's NACH payment system. The Indian fintech firm Nupay acknowledged responsibility for the leak...
Read More » -

Top Cybersecurity Jobs Hiring in September 2025
The cybersecurity field is experiencing high demand for professionals in September 2025, with global opportunities available in various roles and work arrangements, including remote positions. Key roles being recruited for include Application Security Engineers, CISOs, Cloud Security Architects, ...
Read More » -

Secure Your Windows Environments with Runtime CNAPP
Sweet Security has expanded its Runtime CNAPP sensor to include comprehensive protection for Windows cloud environments, offering visibility, threat detection, and automated investigation capabilities previously limited to Linux. The Windows sensor is engineered for cloud deployment using Rust, m...
Read More » -

Top Cybersecurity Jobs Hiring Now | November 2025
The cybersecurity job market offers diverse, high-impact roles globally, from leadership to technical positions, aimed at protecting organizations' digital assets. Key roles include strategic leadership like CISOs defining security roadmaps and technical engineers managing security platforms and ...
Read More » -

Prowler Integrates AI into Security Workflows
Prowler has launched Lighthouse AI and an MCP Server, integrating AI into DevSecOps to speed up risk analysis, compliance, and remediation in multi-cloud environments. These tools enable proactive security by automating decision-making, reducing response times, and embedding security directly int...
Read More » -

NTT DATA and Fortanix Partner to Boost AI and Quantum Security
NTT DATA and Fortanix have launched a Cryptography-as-a-Service solution that combines advanced data security with AI expertise to protect sensitive information across hybrid and multicloud infrastructures against current and future quantum threats. The service emphasizes crypto-agility, enabling...
Read More » -

Securing Australia: How AI and Identity Redefine Cybersecurity
Australian businesses face rapidly evolving cybersecurity threats where traditional defenses are inadequate, with attackers now prioritizing immediate execution over stealth using AI to target identity systems. Cloud environments have become particularly vulnerable, with compromised credentials b...
Read More » -

C-Suite's AI Obsession Fuels Critical Security Gaps
Modern organizations face significant security vulnerabilities due to a disconnect between rapid technological adoption and inadequate security practices, with 34% experiencing AI-related breaches. Many companies rely on outdated, reactive metrics like incident frequency, which only assess damage...
Read More » -

FireCloud Total Access: Hybrid SASE That Scales for All Businesses
FireCloud Total Access unifies four security protections into a single cloud-managed platform, offering enterprise-level Zero Trust security accessible to managed service providers and smaller IT teams through WatchGuard Cloud. It replaces traditional VPNs with identity-based access controls, pro...
Read More » -

Illumio's AI Agent Slashes Alert Fatigue, Speeds Threat Response
Illumio's Insights Agent tackles alert fatigue by providing real-time, tailored alerts and one-click remediation recommendations, helping security teams prioritize and neutralize threats efficiently. The system delivers persona-based AI guidance, offering role-specific risk assessments and action...
Read More » -

Microsoft's 2025 Cyberdefense Report: The New Rules of Engagement
AI is fundamentally reshaping cybersecurity by empowering attackers to refine methods, automate operations, and overwhelm traditional defenses, with nation-state actors increasingly leveraging AI for phishing, vulnerability identification, and malware modification. Identity has become the primary...
Read More » -

Illumio's AI Agent Automates Threat Detection and Containment
Illumio's Insights Agent is an AI-driven tool that provides real-time threat detection and one-click containment to help security teams respond faster and reduce alert fatigue. The Agent uses role-aware intelligence to deliver personalized threat insights and automated remediation steps, tailored...
Read More » -
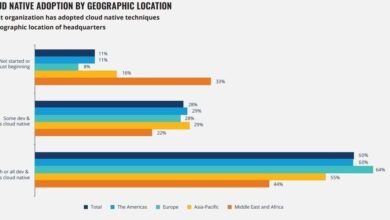
NETSCOUT Enhances Cloud Compliance for Enterprises
NETSCOUT has enhanced its Omnis KlearSight Sensor for Kubernetes to provide deeper visibility for compliance, accelerating threat detection and validating zero-trust policies in response to widespread Kubernetes adoption. The platform addresses compliance risks by capturing packet- and process-le...
Read More » -

Uncover Malicious OAuth Apps in Microsoft 365 with Cazadora
Auditing OAuth applications in Microsoft 365 is critical due to the high risk of malicious apps, which can severely compromise security. Use an open-source script to identify suspicious apps by checking for indicators like mimicry of user names, generic names, or anomalous reply URLs. Huntress re...
Read More » -

CISOs in Survival Mode: Navigating Risk Under Pressure
CISOs face an overwhelming threat environment where most believe a successful breach is inevitable, leading to a focus on rapid response amid frequent, high-impact attacks and low confidence in employee threat detection. Generative AI is a top priority as both a major security risk and a tool for...
Read More » -

Skills Shortages: The Top Cyber Threat Over Hiring
A severe global cybersecurity skills gap, particularly in technical expertise like AI and cloud security, is now a more dangerous threat than general staffing shortages, directly causing significant security incidents for most organizations. The primary obstacles to addressing this gap are a lack...
Read More » -

Top Cybersecurity Jobs Hiring Now | December 2025
The global demand for skilled cybersecurity professionals is exceptionally high across all sectors and experience levels, creating diverse career opportunities. The field encompasses a wide variety of specialized roles, including positions like Application Security Manager, Cloud Security Archite...
Read More » -

Secure Your Cloud with cnspec: Open-Source Policy & Security
cnspec is an open-source tool that provides unified security and compliance scanning across diverse technologies, identifying vulnerabilities and misconfigurations to prioritize fixes. It supports a wide range of targets including cloud platforms, Kubernetes, containers, SaaS applications, infras...
Read More » -

Delinea and Microsoft Partner for Identity Security in Microsoft Store
Delinea has joined the Microsoft Security Store Partner Ecosystem, strengthening their long-term collaboration to simplify cybersecurity adoption for organizations globally. As part of the ecosystem, Delinea contributes to development by providing certified solutions and AI agents that integrate ...
Read More » -

Top Cybersecurity Jobs Hiring Now | October 2025
Cybersecurity careers are thriving with high demand across sectors like energy, finance, and healthcare, requiring technical skills and strategic thinking to protect infrastructure from evolving threats. Key roles include Threat Intelligence Analysts, Application Security Engineers, and Cloud Sec...
Read More » -

Top 10 Data Security Companies to Watch in 2026
Atakama provides a browser security platform for managed service providers, enabling data policy enforcement and threat monitoring through browser extensions and dashboards. AvePoint offers a Data Security Posture Management solution that identifies, classifies, and protects sensitive cloud data ...
Read More »