Topic: supply chain risks
-

Supply Chain Shifts Challenge CPS Security Strategies
Cyber-physical systems face heightened risks due to supply chain instability and regulatory changes, with 46% of organizations experiencing third-party breaches in the past year. External regulations, rather than internal assessments, are driving security strategies, and 76% of organizations expe...
Read More » -

GitHub Flaw: Repositories Can Run Code on Your PC Without Permission
A security flaw in the Cursor extension for Visual Studio Code allows malicious repositories to execute unauthorized code automatically when a project folder is opened, exploiting the autorun feature. This vulnerability enables attackers to steal sensitive data like authentication tokens, tamper ...
Read More » -

Cyber Security Month: Are You at Risk of a Cyber Crash?
This October's Cyber Security Awareness Month is a critical call to action for Australian businesses, emphasizing the urgent need to address digital vulnerabilities highlighted by recent data breaches and sophisticated phishing attacks. Organizations must modernize legacy technology and implement...
Read More » -

LLMs Infiltrate Your Stack: New Risks at Every Layer
The integration of LLMs into enterprises requires a fundamental security shift, moving from treating models as intelligent brains to viewing them as untrusted compute, which is critical for establishing robust trust boundaries. Key technical vulnerabilities include prompt injection, sensitive dat...
Read More » -

Solar Power Boom Sparks Cybersecurity Threat
The rapid expansion of solar energy infrastructure introduces significant cybersecurity vulnerabilities, with inverters, monitoring platforms, and grid-connected devices becoming critical targets for malicious actors aiming to disrupt power supply and undermine renewable energy confidence. Real-w...
Read More » -

Australia Poised to Become World's Second-Largest Rare Earth Supplier
Australia is poised to become the world's second-largest rare earth supplier, capitalizing on growing demand for these elements in renewable energy and technology sectors, with projections to meet 15-20% of global neodymium and praseodymium demand outside China. China currently dominates the rare...
Read More » -

Safeguarding the Internet's Lifeline: Protecting Global Cables
Submarine cables carry over 95% of global data but face threats from geopolitical friction, supply chain vulnerabilities, and slow repair processes, requiring public-private collaboration for reinforcement. Building resilience through strategic redundancy by laying diverse cables is hindered by h...
Read More » -

Enterprise Security's Triple Threat: Cybercrime, AI, and Supply Chains
The cybersecurity landscape is defined by a triple threat from advanced cybercrime, the dual risks and benefits of artificial intelligence, and pervasive supply chain vulnerabilities, forcing a strategic shift in defense. AI is both a critical security tool for detection and response and a major ...
Read More » -

Railway Cybersecurity: Hackers Push the Limits
Railway networks are increasingly vulnerable to cybersecurity threats due to digital transformation, which introduces risks like remote system manipulation and potential accidents. Outdated infrastructure and extended equipment lifecycles complicate security, with many systems running on obsolete...
Read More » -

ImmuniWeb Unveils New Cyber Threat Intelligence Service
ImmuniWeb Discovery has launched a new Cyber Threat Intelligence (CTI) service that monitors threats to an organization's assets and tracks broader cybercrime trends, regulatory changes, and supply chain risks. The service provides actionable intelligence on diverse threat actors, including APT g...
Read More » -

The Energy Sector's Urgent Cybersecurity Crisis
The global energy sector is increasingly targeted by sophisticated cyberattacks, threatening power grids, national security, and economic stability due to rising electricity demand and vulnerabilities. Recent incidents, including a blackout in Spain and Portugal and attacks by groups like Sandwor...
Read More » -

Intel 471 Launches Verity471: Next-Gen Cyber Threat Intel Platform
Intel 471 launched Verity471, a unified cyber threat intelligence platform that integrates intelligence offerings into a single interface to enhance security operations and threat response. Verity471 provides actionable insights through three portfolios: Cyber Threat Exposure (identifies vulnerab...
Read More » -

Protecting Connected Vehicles from Cyber Threats
The rise of connected vehicles has revolutionized fleet management but introduced significant cybersecurity risks, requiring zero-trust approaches, real-time monitoring, and AI-driven defenses. Securing connected vehicle systems is challenging due to multiple attack vectors like telematics and GP...
Read More » -

Nvidia's Q4: A Make-or-Break Moment for AI Hardware
Nvidia's upcoming quarterly report is a key indicator for the AI hardware sector, with its dominant role in powering AI models having fueled its massive valuation, but the focus is now shifting to the sustainability of the broader AI investment cycle. Analysts expect another quarter of staggering...
Read More » -
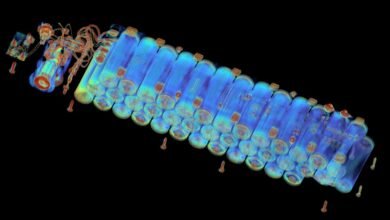
X-Ray Scans Expose Cheap Battery Dangers
A study using industrial X-ray scanning revealed that cheap and counterfeit lithium-ion batteries often contain dangerous manufacturing flaws, significantly increasing the risk of fires and explosions compared to major-brand batteries. The investigation found hazardous defects, such as negative a...
Read More »