Topic: cyber resilience
-

Wasabi's Covert Copy Boosts Cloud Storage Security
Wasabi's new Covert Copy feature creates a hidden, locked backup of cloud storage that is invisible and inaccessible to attackers, enhancing ransomware defense. It requires multi-user authentication to access the protected data and is designed for simple, cost-effective implementation with no egr...
Read More » -

Commvault's New AI Makes Backup and Recovery Conversational
Commvault introduces conversational AI technology that enables businesses to manage data protection tasks using natural language commands through integration with enterprise AI assistants. The system is secured by the Model Context Protocol (MCP) server, which ensures interactions comply with org...
Read More » -

Secure Your Data Offline with Acronis Cyber Protect Local
Acronis Cyber Protect Local is an all-in-one on-premises platform that integrates data backup, cybersecurity, and endpoint management for IT and OT environments, ensuring data sovereignty and reducing complexity. It supports legacy systems and modern hypervisors, offering broad compatibility, AI-...
Read More » -

Pure Storage Boosts Cyber Resilience with New Innovations & Partnerships
Pure Storage is enhancing cybersecurity by embedding native threat detection into its storage platform and forming strategic partnerships to proactively identify threats and enable faster recovery. The company is integrating with security leaders like CrowdStrike and Superna to provide real-time ...
Read More » -

Quantify Cyber Risk to Win Executive Buy-In
CISOs should translate cyber risks into financial terms to secure executive approval for security budgets by demonstrating potential monetary losses and investment returns. The evolving threat landscape includes AI-driven attacks and defenses, requiring constant vigilance and adaptation in cybers...
Read More » -

Commvault Revolutionizes Cyberattack Recovery
Commvault's Cleanroom Recovery and Cloud Rewind platforms enable secure, isolated testing and rapid restoration of data and entire cloud applications to combat cyberattacks. An independent study validates that Commvault's solutions reduce recovery times by 99%, accelerate infrastructure rebuildin...
Read More » -

Cognizant and Rubrik Partner to Deliver Business Resilience-as-a-Service
Cognizant and Rubrik have launched a Business Resilience-as-a-Service (BRaaS) solution, offering a flexible, subscription-based model to help enterprises recover from cyberattacks and ensure operational continuity. The rise of AI increases IT complexity and expands the attack surface, necessitati...
Read More » -

Cyber Security Month: Are You at Risk of a Cyber Crash?
This October's Cyber Security Awareness Month is a critical call to action for Australian businesses, emphasizing the urgent need to address digital vulnerabilities highlighted by recent data breaches and sophisticated phishing attacks. Organizations must modernize legacy technology and implement...
Read More » -

Navigating Cloud Complexity for Cyber Resilience
Cloud-first strategies now dominate enterprise infrastructure, with 85% of business applications projected to be SaaS-based, driven by IoT data growth and rapid AI adoption requiring immense processing and storage. The shift to cloud introduces significant security and management challenges, incl...
Read More » -

UAE Leads Cybersecurity and Digital Innovation at GITEX 2025
The UAE is showcasing its leadership in cybersecurity and digital innovation at GITEX GLOBAL 2025, emphasizing international cooperation and investment in its growing digital ecosystem. Key technologies highlighted include artificial intelligence, quantum computing, and advanced cybersecurity, wh...
Read More » -

Pure Storage Unveils 3-Tier Data Cloud Strategy to Do More With Less
Pure Storage has introduced an Enterprise Data Cloud strategy to unify data management, helping organizations leverage data for AI, improve performance, and eliminate data silos. The strategy is built on three pillars: an Intelligent Control Plane for automation and AI-driven management, a Unifie...
Read More » -
Securing Legacy Medical Devices Beyond Patching
Legacy medical devices without security patches require protective barriers and close collaboration with vendors to manage risks and plan phased replacements. A risk-based security approach supports compliance by focusing on proactive measures, staff education, and strategic risk mitigation rathe...
Read More » -

Post-Quantum Security: Why You Need It Now
Australia is at a critical technological juncture where quantum computing presents both opportunities and a fundamental risk to existing cryptographic systems, threatening the security of sensitive data. Quantum computers can break widely used encryption standards like RSA and ECC, potentially de...
Read More » -
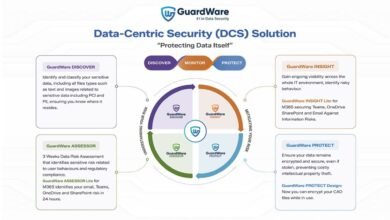
GuardWare Launches World-First Solution to Permanently Stop Data Theft
GuardWare has launched PROTECT, a pioneering encryption software suite that persistently secures sensitive data during active use, enabling secure movement in supply chains and remote file destruction. PROTECT addresses vulnerabilities in unstructured data files by employing a data-centric securi...
Read More » -

Rethink Network Visibility for Australia's Critical Infrastructure
Government agencies in Australia and the Asia Pacific face escalating cybersecurity threats due to the deep integration of digital and physical infrastructure, making public services like transportation and healthcare prime targets for sophisticated attacks. The convergence of IT and OT systems, ...
Read More » -

Why Satellite Cybersecurity Is Everyone's Concern
Satellite cybersecurity has become a critical global issue due to the widespread reliance on these systems for communications, navigation, finance, and national security, with many older satellites lacking modern security protections. Vulnerabilities exist across all segments of space systems, in...
Read More » Australia's Cyber Crisis: A Call to Action for Businesses
Australian businesses face sophisticated cyber campaigns aimed at crippling economic stability and critical national functions, moving beyond simple data theft to cause national paralysis. The conflict in Ukraine demonstrated that cyber warfare is synchronized with military operations, targeting ...
Read More »-

Exposure Management: The New Boardroom Test
Cybersecurity is now a critical board-level concern due to regulatory, investor, and reputational pressures, with exposure management providing a framework to address the gap between investment and escalating breaches. Exposure management shifts focus from counting resolved alerts to continuously...
Read More » -

Arctera InfoScale Uses AI to Detect and Stop Ransomware
Arctera's InfoScale platform now uses AI to detect and neutralize ransomware threats in real time by analyzing behavioral patterns across applications, storage, and infrastructure. The system provides full-stack visibility and application-aware actions, enabling immediate protective measures to l...
Read More » -

Your Cybersecurity Mindset Is the Real Vulnerability
The primary cybersecurity vulnerability is not technical but organizational, stemming from collective mindset and culture rather than outdated systems or weak passwords. Building a true security culture requires integrating cybersecurity into daily workflows and decision-making, fostering shared ...
Read More » -

Jordan's Cybersecurity: Building Human-Centric Resilience
Jordan is advancing its digital security by emphasizing the need for a well-informed society, viewing public awareness and education as essential for sustainable cybersecurity alongside technological measures. The nation is addressing a shortage of cybersecurity professionals through educational ...
Read More » -

Pure Storage Unifies Data for AI Control
Pure Storage has upgraded its platform to unify data management across hybrid cloud and on-premises environments, addressing the need for seamless data control to support AI innovation. A key enhancement is the expansion of the Enterprise Data Cloud into the public cloud with Pure Storage Cloud, ...
Read More » -

Discover Role-Based Cybersecurity Solutions for Your Team
Immersive's AI-powered Lab Builder enables customized, role-based cybersecurity training through realistic simulations, addressing the gap in workforce upskilling where only 39% of efforts focus on training. The tool uses AI to generate real-time, threat-specific labs (Theory and Practical Labs) ...
Read More » -

Unseen Dangers of Generative AI
Businesses are rapidly adopting AI for productivity but are dangerously unprepared for the unique cybersecurity risks it introduces, such as vulnerabilities from generative models. A significant gap exists between AI investment and security readiness, with most organizations lacking processes to ...
Read More » -

Building Cyber Defenses: How Nations Secure Their Digital Borders
Cyberspace is now recognized as the fifth domain of warfare, with nations integrating cyber operations into military and intelligence activities, yet accurately attributing attacks remains a major challenge. Active cyber defense strategies, such as threat hunting, are essential for resilience, en...
Read More » -

Veeam Appliance: Enhanced Data Protection Solutions
Veeam Software has introduced a fully pre-built and pre-hardened software appliance that eliminates manual setup, OS patching, and Windows licensing, offering a secure, ready-to-use data protection platform. The hardware-agnostic appliance can be deployed across physical, virtual, or cloud enviro...
Read More » -

Australia's 2024-2025 Cyber Threat Report Reveals Key Security Trends
Australia is experiencing a sharp increase in cybersecurity threats, driven by its growing reliance on internet-connected technology and targeting by both criminal and state-sponsored actors, leading to significant financial losses and a rise in incidents. State-backed cyber actors and cybercrimi...
Read More » -

Unlock Cyber Resilience: Security Awareness Month 2025
Cybersecurity Awareness Month emphasizes the need for collective digital defense as identity-based attacks, accounting for nearly 80% of incidents, exploit compromised credentials to bypass traditional perimeter security. Adopting zero trust principles, such as least privilege and just-in-time ac...
Read More » -

Cybersecurity Leaders Hide Cyber Incidents From Executives
Corporate cybersecurity leaders are increasingly concealing security incidents from their own executive leadership and boards, creating a dangerous gap in understanding the organization's true risk profile and leading to decisions based on incomplete information. Nation-state cyberattacks are a p...
Read More » -

UK Report: Hold Software Makers Liable for Security Flaws
The UK Business and Trade Committee proposes making software companies legally accountable for security flaws, arguing that voluntary guidelines are inadequate to protect the nation's economy from rising cyber-attacks. Recent high-profile breaches, such as those affecting M&S and the Co-op, have ...
Read More » -

Netpoleon, Vectra AI Strengthen ANZ Cybersecurity Alliance
Netpoleon and Vectra AI have expanded their strategic alliance to deliver advanced AI-driven Network Detection and Response solutions across Australia and New Zealand, enhancing cybersecurity capabilities for enterprise clients and government agencies. Vectra AI has been recognized as a Leader in...
Read More » -

Bitdefender & CYPFER: End-to-End Cyber Resilience for Businesses
Bitdefender and CYPFER have partnered to provide end-to-end cyber resilience, integrating incident response, forensic investigation, and rapid recovery into Bitdefender's security portfolio for businesses of all sizes. The collaboration combines Bitdefender's threat detection and intelligence wit...
Read More » -

Ootbi Mini: Zero Trust, Unbreakable Data Security
Object First launched the Ootbi Mini, a compact, immutable storage appliance designed to protect Veeam backup data from ransomware, targeting remote offices and small businesses with capacities up to 24TB. The device is built on a zero trust architecture, ensuring complete data immutability and r...
Read More » -

Illumio Joins the Microsoft Sentinel Partner Ecosystem
Illumio has joined the Microsoft Sentinel partner ecosystem, integrating its breach containment capabilities to enhance threat detection and response in hybrid and multi-cloud environments. The partnership leverages Microsoft Sentinel's AI-ready platform, including its unified data lake and Secur...
Read More » -

Rubrik & Okta Unite to Stop Ransomware with Identity Recovery
Rubrik and Okta have partnered to launch Rubrik Okta Recovery, offering automated, immutable backups and granular restoration for Okta Identity Provider environments to combat ransomware and ensure swift recovery. This solution provides operational resilience by protecting Okta tenants from accid...
Read More » -

BEAMTEL Launches CyberPlatform to Boost Morocco's Cybersecurity
BEAMTEL has launched CyberPlatform, Morocco's first fully Arabic-language cybersecurity education portal, to enhance national cyber resilience and make digital safety knowledge widely accessible. The platform offers tailored resources for various groups, including individuals, businesses, and gov...
Read More » -

CISA Launches New Tool to Streamline Incident Response
CISA and MITRE introduced the Eviction Strategies Tool, a free resource for organizations. This tool empowers cyber defenders to swiftly create customized plans for removing threats from compromised systems. By integrating extensive countermeasure data, it simplifies complex incident response, aiming to significantly reduce attacker presence and bolster overall cyber defenses nationwide.
Read More » -

BarracudaONE Launches AI Tools to Simplify MSP Security
Barracuda Networks has upgraded its BarracudaONE platform with AI-driven features to simplify security management, automate billing, and enhance operational efficiency for managed service providers. Key enhancements include bulk remediation for email threats to reduce response times and PSA integ...
Read More » -

Securing Australia: How AI and Identity Redefine Cybersecurity
Australian businesses face rapidly evolving cybersecurity threats where traditional defenses are inadequate, with attackers now prioritizing immediate execution over stealth using AI to target identity systems. Cloud environments have become particularly vulnerable, with compromised credentials b...
Read More » -

Top Cybersecurity Threats to Watch in 2025
The cybersecurity landscape in 2025 will be shaped by sophisticated threats from AI-driven attacks, quantum computing risks, and aggressive geopolitical cyber campaigns. AI-powered tools enable autonomous threat agents to launch personalized phishing, adaptive malware, and large-scale attacks, wh...
Read More » -

Unite to Conquer Cybersecurity Threats: Key Partnerships
Global cyberattacks have tripled since 2023, targeting critical infrastructure in nations like the UAE, Ukraine, and Israel, highlighting the urgent need for precise data and AI-driven defenses. The UAE's cybersecurity strategy emphasizes education, public awareness, and five key pillars—partners...
Read More » -

Barracuda Assistant: Turbocharge Your Security Operations
Barracuda Assistant is an AI-driven tool integrated into the BarracudaONE platform, designed to accelerate security operations and enhance cyber resilience, productivity, and ROI. It simplifies security workflows by providing a unified interface for threat investigation and response, reducing hum...
Read More » -

UK Cyber Shield Blocks 1 Billion Attacks on Telecom Networks
The UK's National Cyber Security Centre (NCSC) has blocked nearly one billion cyberattacks in a year using its proactive "Share and Defend" service, which protects national telecom infrastructure by filtering malicious websites. The system works by gathering threat intelligence from partners and ...
Read More » -

UK's New Cyber Bill to Fortify Critical Services
The UK government has introduced the Cyber Security and Resilience Bill to modernize cybersecurity laws and enhance national defenses against growing cyber threats, updating the 2018 NIS Regulations. The legislation expands regulatory scope to include managed service providers, data centers, digi...
Read More » -

Hacktivist DDoS Attacks Surge Against Government Sites
Hacktivist-driven DDoS attacks were the most frequent cybersecurity incidents in the public sector, accounting for 60% of cases, though they were not the most damaging. Data breaches and ransomware, often by cybercriminals and state actors, caused more severe impacts, targeting sensitive services...
Read More » -

U.S.-UAE AI Chiefs Forge Tech Partnership
AI integration is a top national priority for the UAE, central to its strategy for pioneering digital governance and achieving strategic ambitions. A high-level UAE delegation visited the U.S. to foster international collaboration, share best practices, and build partnerships with leading tech fi...
Read More » -

3 Must-Haves to Survive a Cyberattack
Swift and effective response to a cyberattack depends on having clarity, control, and a reliable lifeline already in place. Clarity involves real-time detection and understanding of the incident's scope, enabling informed decisions to isolate and manage threats. Control means the ability to conta...
Read More » -

ENISA to Lead €36m EU-Wide Cybersecurity Response Initiative
The EU has allocated €36 million to ENISA to coordinate a cybersecurity response initiative, enhancing collective resilience against large-scale cyber incidents across member states and partner nations. ENISA will manage the EU Cybersecurity Reserve, a virtual pool of private sector services, to ...
Read More » -

China's Salt Typhoon Hackers Target Dutch Telecoms, Netherlands Confirms
Dutch intelligence confirmed that the Chinese state-sponsored hacking group Salt Typhoon infiltrated telecommunications and internet providers in the Netherlands, posing a sophisticated threat to critical infrastructure. The hackers compromised routers of smaller Dutch internet service providers ...
Read More » -

Salesforce, CentreStack Hit by Hackers in Zero-Day Attacks
Major platforms like Salesforce and CentreStack have been compromised by zero-day vulnerabilities, underscoring the need for timely patching and robust security measures. Recent incidents include the Cl0p gang exploiting Oracle E-Business Suite flaws and North Korean hackers stealing over $2 bill...
Read More »