Topic: data protection
-

TikTok Deal Finalized After Months of Negotiations
A new joint venture has been established to protect U.S. TikTok user data and the platform's core algorithm, housing them within Oracle's secure U.S. cloud infrastructure. The entity will enforce strict data privacy, cybersecurity, and software assurance protocols, with oversight from independent...
Read More » -

FalconStor Habanero: Compliant IBM Power Backup Made Simple
FalconStor Habanero is a new SaaS solution designed to provide secure, compliant offsite data protection and disaster recovery for businesses using on-premises IBM Power systems, without requiring new hardware or changes to existing backup workflows. The fully managed service offers immutable cyb...
Read More » -

CRA & Ehsan Center Host Digital Privacy Workshop for ITU Anniversary
The Communications Regulatory Authority and Ehsan Center organized a workshop on personal data protection and secure mobile usage, targeting elderly individuals to enhance their digital safety skills. The initiative supports Qatar National Vision 2030 by fostering responsible technology use and b...
Read More » -

Proofpoint's 4 New Innovations to Secure the Future of Work
The rise of the agentic workspace, where humans and AI agents collaborate, introduces new security challenges that require a fresh, human-centric security approach. Proofpoint has launched innovations to protect AI interactions, including Prime Threat Protection to block malicious prompt injectio...
Read More » -

Secure Your Phone Abroad: How 1Password's Travel Mode Protects Your Data
US Customs and Border Protection is conducting a record number of electronic device searches, raising privacy concerns for travelers and leading to potential detentions or denied entries based on digital content. 1Password's Travel Mode offers a solution by allowing users to hide sensitive vaults...
Read More » -

ADGM Unveils New Public Interest Rules to Boost Data Protection
ADGM has introduced new data protection regulations that provide clear guidelines for processing sensitive personal data in the public interest, particularly in sectors like insurance and education. The regulations include specific conditions and safeguards for handling sensitive data without con...
Read More » -

Secure Your Luxury Logistics: A Counterintelligence Approach
In luxury logistics, protecting sensitive data like client identities and shipping routes is as crucial as securing physical cargo, requiring a multi-layered defense strategy. Key security measures include multi-factor authentication, endpoint protection, and employee training to combat threats l...
Read More » -

DataLocker Enhances Security with DL GO & MySafeConsole
DataLocker has launched the DL GO encrypted USB drive and MySafeConsole cloud platform, offering enterprise-level security features at an accessible price for individuals and small businesses. The DL GO drive uses AES-256 XTS hardware encryption, supports biometric authentication, and has a rugge...
Read More » -

iRobot's New Chinese Owner Vows US Data Stays in America
iRobot is creating a new U.S. subsidiary, iRobot Safe, to manage and protect American consumer data separately from its Chinese parent company, Picea Robotics. The subsidiary will have independent U.S. leadership to ensure domestic data handling remains under U.S. jurisdiction, addressing data se...
Read More » -

Groupe Rocher CISO: Modernizing Retail Cybersecurity
Retail cybersecurity requires balancing data protection, network management, and consumer trust, while facing evolving threats across both online and in-store systems. A common misalignment exists between stated security goals and actual risks, necessitating proactive strategies like threat intel...
Read More » -

Bluesky's 'Privacy-First' Contact Import: Here's How It Works
Bluesky's "Find Friends" feature prioritizes privacy by requiring mutual consent and active participation from both users for a match to occur. The system uses phone number verification and cryptographic hashing to protect contact data, preventing unauthorized access or probing. Users maintain fu...
Read More » -

Wasabi's Covert Copy Boosts Cloud Storage Security
Wasabi's new Covert Copy feature creates a hidden, locked backup of cloud storage that is invisible and inaccessible to attackers, enhancing ransomware defense. It requires multi-user authentication to access the protected data and is designed for simple, cost-effective implementation with no egr...
Read More » -

Bedrock Data Adds AI Governance and Natural-Language Policy Tools
Bedrock Data has launched ArgusAI for AI governance and Natural Language Policy to help businesses manage AI-related risks and compliance by securing sensitive information. ArgusAI provides deep visibility into AI data interactions and evaluates safeguards to prevent data leakage, while Natural L...
Read More » -
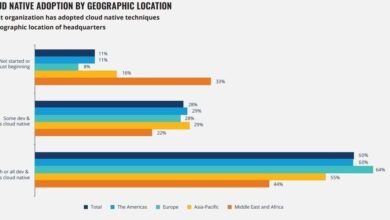
NETSCOUT Enhances Cloud Compliance for Enterprises
NETSCOUT has enhanced its Omnis KlearSight Sensor for Kubernetes to provide deeper visibility for compliance, accelerating threat detection and validating zero-trust policies in response to widespread Kubernetes adoption. The platform addresses compliance risks by capturing packet- and process-le...
Read More » -

Commvault's New AI Makes Backup and Recovery Conversational
Commvault introduces conversational AI technology that enables businesses to manage data protection tasks using natural language commands through integration with enterprise AI assistants. The system is secured by the Model Context Protocol (MCP) server, which ensures interactions comply with org...
Read More » -

Veeam Data Cloud for MSPs: Boost Partner Data Resilience
Veeam Data Cloud for MSPs is a secure, multi-tenant SaaS platform that simplifies data protection and supports scalable growth for managed service providers. The platform offers unified management, effortless scalability, and enhanced security features to reduce operational complexity and acceler...
Read More » -

Commvault Revolutionizes Cyberattack Recovery
Commvault's Cleanroom Recovery and Cloud Rewind platforms enable secure, isolated testing and rapid restoration of data and entire cloud applications to combat cyberattacks. An independent study validates that Commvault's solutions reduce recovery times by 99%, accelerate infrastructure rebuildin...
Read More » -

Xage Fabric: Secure Your Data from Unauthorized Access
Businesses face significant security challenges when adopting AI, including data breaches and unauthorized access, which traditional measures often fail to address effectively. Xage Security has introduced a zero trust platform designed specifically for AI environments, offering identity-centric,...
Read More » -

Liquid C2 & AvePoint Partner to Accelerate Africa's Cloud Transformation
A strategic partnership between Liquid C2’s Cloudmania and AvePoint aims to accelerate secure cloud adoption across Africa by integrating advanced data protection and governance tools. The collaboration enhances Cloudmania’s Microsoft-based offerings, providing businesses with improved security, ...
Read More » -

Urgent: Change Your Plex Password Now
Plex has experienced a security breach where an unauthorized party accessed customer data, including email addresses, usernames, and securely hashed passwords. The company has addressed the vulnerability and recommends users immediately reset their passwords and enable two-factor authentication f...
Read More » -

Google Sues SerpApi for Scraping Search Results
Google has sued SerpApi for commercially scraping and reselling its search results, alleging violations of its terms of service and legal precedent to protect its proprietary data, which is crucial in the AI era. The lawsuit highlights a market demand for search data that Google doesn't provide v...
Read More » -

Commvault Launches Data Rooms to Link Backup Data with AI
Commvault's Data Rooms provide a secure environment for businesses to connect backup data to AI platforms and data lakes, bridging data protection with activation while minimizing risk. The solution addresses challenges in data accessibility and trust by offering built-in governance, automated cl...
Read More » -

Veeam Data Cloud Simplifies Microsoft 365 & Entra ID Protection for MSPs
Veeam Software introduced Veeam Data Cloud for MSPs, a SaaS platform that simplifies data protection for Microsoft 365 and Entra ID workloads through secure, scalable solutions. The platform offers key benefits including effortless scalability, built-in security, actionable insights, and centrali...
Read More » -

ExaGrid 7.4.0 Adds New MSP Features for Tiered Backup Storage
ExaGrid's Version 7.4.0 introduces features tailored for Managed Service Providers (MSPs), enhancing data protection and streamlining billing and operations on its Tiered Backup Storage platform. The update allows MSPs to host multiple clients securely on a single system with dedicated shares, en...
Read More » -

AI SSD Subscription Fights Ransomware at Hardware Level
Flexxon has launched the X-Phy Guard Solution, an AI-integrated SSD designed as a final defense against cyberattacks like ransomware, targeting high-security sectors with a subscription starting at $249 annually. The drive's AI engine monitors for threats such as encryption patterns and physical ...
Read More » -

Trump Approves $14B TikTok Deal, Cedes 80% to US Investors
President Trump approved a $14 billion deal transferring 80% ownership of TikTok's U.S. operations to American investors, addressing national security concerns and ensuring the app's future in the country. The agreement reduces Chinese parent company ByteDance's stake to 19.9% and includes safegu...
Read More » -

AI's Speed Demands Faster Data Security Now
Generative AI is being rapidly adopted by businesses for innovation, but it introduces significant data security challenges, especially concerning data integrity and confidentiality. The reliance on high-quality data makes AI systems vulnerable to integrity-based threats, such as data tampering, ...
Read More » -

GDPR Training: Turn Compliance into Competitive Advantage
Despite significant investment in GDPR compliance, many businesses struggle with employee security practices, risking heavy fines and reputational damage. Effective training requires role-specific, continuous education that integrates practical tools like password managers to foster lasting behav...
Read More » -

ID Verification Laws Are Creating New Security Breaches
New ID verification laws are forcing businesses to collect sensitive personal data like government IDs, often without adequate security infrastructure, conflicting with the cybersecurity principle of minimal data collection. A Discord data breach exposed government ID images collected for age ver...
Read More » -

Audit AI Actions, Not Its Thoughts
AI presents a dual challenge for CISOs, offering defensive capabilities like fraud detection while adversaries use it for malicious purposes, requiring organizations to defend both with and against it. Ensuring AI tools are auditable, explainable, and resilient is difficult due to their complex d...
Read More » -

OpenText AI Boosts Enterprise Security for Identity, Data & Apps
OpenText has launched a suite of cybersecurity enhancements that integrate AI into security workflows, unifying protection across identity, data, applications, and forensics with tools like Core Threat Detection and Core Identity Foundation. The CE 25.4 release strengthens compliance with built-i...
Read More » -

AI Cloud Protect: Next-Gen Enterprise Security by Check Point & NVIDIA
AI Cloud Protect is a joint security solution from Check Point and NVIDIA designed to safeguard on-premises enterprise AI environments, protecting the entire AI lifecycle from development to inference without compromising performance. The solution addresses urgent security needs, as over half of ...
Read More » -

Cognizant and Rubrik Partner to Deliver Business Resilience-as-a-Service
Cognizant and Rubrik have launched a Business Resilience-as-a-Service (BRaaS) solution, offering a flexible, subscription-based model to help enterprises recover from cyberattacks and ensure operational continuity. The rise of AI increases IT complexity and expands the attack surface, necessitati...
Read More » -

FinWise Breach: Why Encryption Is Your Final Defense
The 2024 FinWise data breach was caused by a former employee who exploited retained login credentials, accessing sensitive data for 689,000 customers undetected for over a year. The breach exposed inadequate security measures, including possible encryption failures and lack of monitoring for irre...
Read More » -

Global Compliance Strategy: A Cross-Border Blueprint
Global compliance requires a forward-thinking strategy that integrates data protection with operational efficiency to avoid penalties and build trust. An ideal compliance platform must blend rigorous data protection with user-friendly design, ensuring scalability and adherence to international re...
Read More » -

F5 Acquires CalypsoAI to Secure Generative AI Systems
F5 is acquiring CalypsoAI for $180 million to enhance its security offerings with specialized capabilities for protecting generative AI systems against emerging threats. The acquisition aims to integrate CalypsoAI's technology into F5's platform, providing real-time threat defense, data security,...
Read More » -
Cloudflare Balances Data Security with AI Access
Cloudflare One has been enhanced to help businesses securely integrate and manage generative AI tools while maintaining data protection and compliance standards. New features include AI Security Posture Management (AI-SPM), offering discovery of AI usage patterns, protection against unapproved AI...
Read More » -

Germany Launches Quantum-Secure National ID Cards
Germany is launching a new generation of national ID cards with quantum-resistant security features to protect against future threats from quantum computers. The upgrade involves a two-phase rollout, starting with quantum-resistant digital signatures and transitioning to a fully quantum-safe syst...
Read More » -

Veeam Appliance: Enhanced Data Protection Solutions
Veeam Software has introduced a fully pre-built and pre-hardened software appliance that eliminates manual setup, OS patching, and Windows licensing, offering a secure, ready-to-use data protection platform. The hardware-agnostic appliance can be deployed across physical, virtual, or cloud enviro...
Read More » -

EU Investigates xAI Over AI-Generated Explicit Content
European regulators have launched a formal GDPR investigation into X's Grok AI chatbot, focusing on its generation of non-consensual explicit imagery and deepfakes using EU personal data. The probe, led by Ireland's Data Protection Commission, was triggered by widespread complaints and media repo...
Read More » -

Android's New Lockout Feature Hardens Device Security
Google has enhanced Android's device theft protection with stronger authentication, including a more robust Failed Authentication Lock and increased lockout times after incorrect login attempts, making brute-force attacks significantly harder. The update expands the Identity Check feature to requ...
Read More » -

TikTok U.S. Deal With Oracle, Silver Lake to Close in January
TikTok and ByteDance have formed a U.S.-based joint venture to comply with a "divest-or-ban" law, with the new entity set to begin operations in January 2026. The joint venture's ownership is majority U.S.-based, with a consortium including Oracle, Silver Lake, and MGX holding 50%, while ByteDanc...
Read More » -

TikTok Ban: Latest Updates on the US Shutdown and Return
TikTok has resolved a U.S. legal challenge by creating a new joint venture, TikTok USDS Joint Venture LLC, set to launch in January 2026, with partners including Oracle. This new U.S.-based entity will take full control over American user data, algorithm security, content moderation, and platform...
Read More » -

UK Fines LastPass £1.2 Million Over 2022 Data Breach
The UK's Information Commissioner's Office fined LastPass £1.2 million for failing to protect user data, leading to a 2022 breach that compromised personal details of 1.6 million individuals. The breach occurred through a multi-stage attack where a hacker compromised an employee's device, stole e...
Read More » -

Portugal's New Cybercrime Law Shields Security Researchers
Portugal has enacted a safe harbor law, exempting ethical cybersecurity research from prosecution if it is conducted responsibly and without seeking economic benefit. The law requires researchers to act proportionally, avoid harmful methods like data theft, and confidentially report vulnerabiliti...
Read More » -

Trend Vision One: Proactive AI Security for Your Environment
Trend Vision One's AI Security Package, launching in December, provides centralized exposure management and protection across the entire AI application lifecycle, from development to runtime operations. The solution addresses the limitations of conventional security tools by offering specialized ...
Read More » -

Discord Data Breach: Vendor Denies Being Hacked
5CA denies experiencing a data breach in its systems and clarifies it never handled government-issued IDs for the affected client, maintaining secure operations under strong data protection protocols. An ongoing forensic investigation, involving the client and cybersecurity experts, indicates the...
Read More » -

Enhance Security with Netskope UZTNA's Dynamic Policy Controls
Netskope's Universal ZTNA platform now integrates Private Access and Device Intelligence, offering deeper threat inspection and enabling businesses to replace outdated technologies like VPNs and NACs. The solution extends protection to IoT and OT devices with built-in device intelligence and embe...
Read More » -

Tunisie Telecom Secures ISO 27001:2022 for Enhanced Data Security
Tunisie Telecom has achieved ISO/IEC 27001:2022 certification for its Information Security Management System, validated by TÜV Rheinland, highlighting its commitment to top-tier security protocols. The certification applies to all processes of the Customer Relations Directorate, ensuring customer...
Read More » -

Imgur Blocks UK Users in Surprise Geo-Ban
Imgur has blocked all access for UK users, preventing them from logging in, viewing, or uploading content as of September 30, 2025, following a warning from the UK's data protection authority. The UK's Information Commissioner’s Office is investigating Imgur over its handling of children's data a...
Read More »