Topic: information security
-

Hiring Now: Top Cybersecurity Jobs for September 2025
The cybersecurity job market is expanding rapidly due to increasing cyber threats, with high demand for specialized roles across various sectors and countries. Key positions include Chief Information Security Officers (CISOs) who develop security strategies and manage risk, and other roles like C...
Read More » -

Tunisie Telecom Secures ISO 27001:2022 for Enhanced Data Security
Tunisie Telecom has achieved ISO/IEC 27001:2022 certification for its Information Security Management System, validated by TÜV Rheinland, highlighting its commitment to top-tier security protocols. The certification applies to all processes of the Customer Relations Directorate, ensuring customer...
Read More » -

DHS Data Hub Leaked Sensitive Intel to Thousands
A misconfigured DHS online platform exposed 439 classified intelligence products to thousands of unauthorized users, including government staff, contractors, and foreign nationals, over two months in early 2023. The leaked data included sensitive reports on cybersecurity threats, foreign hacking,...
Read More » -

Pentagon report: Pete Hegseth violated military policies
A Pentagon investigation found former Defense Secretary Pete Hegseth violated DoD protocols by using a personal messaging app to discuss sensitive military information, risking its compromise. The inquiry, hampered by the app's auto-delete function, stemmed from a group chat that inadvertently in...
Read More » -

Australian Clinical Labs Fined for Medlab Pathology Data Breach
Australian Clinical Labs was fined $5.8 million for a 2022 data breach affecting over 223,000 people, marking the first civil penalties issued under the Privacy Act 1988. The penalties were imposed for failing to protect personal information, assess the breach promptly, and report it to the Commi...
Read More » -

Can Anthropic's AI Safety Plan Stop a Nuclear Threat?
Anthropic is collaborating with US government agencies to prevent its AI chatbot Claude from assisting with nuclear weapons development by implementing safeguards against sensitive information disclosure. The partnership uses Amazon's secure cloud infrastructure for rigorous testing and developme...
Read More » -

Apple iPhones and iPads Cleared for Classified Government Data
Apple iPhones and iPads running iOS/iPadOS 26 have received official NATO certification to handle classified government data, marking the first time a mainstream consumer product meets such stringent security standards out of the box. This certification, built on a prior German government evaluat...
Read More » -

Asahi Data Breach Exposes 1.5 Million Customers
Asahi Group Holdings confirmed a September cyberattack affected about 1.9 million individuals, exposing personal details like names, addresses, and contact information, but no financial data was compromised. The Qilin ransomware group claimed responsibility, releasing stolen data samples after th...
Read More » -

Coupang CEO Resigns Amid Police Raid Over Data Breach
Coupang's CEO resigned after a massive data breach affecting 33.7 million users, far more than initially reported, and publicly accepted responsibility for the incident and its handling. South Korean police raided Coupang's headquarters and are investigating a former employee, while U.S.-based pa...
Read More » -

Asahi Cyber-Attack: 1.5 Million Customers' Data Breached
The Asahi Group suffered a major cybersecurity breach in September 2025, compromising personal data of nearly two million individuals, including names, addresses, and contact details, but not credit card information. The ransomware attack by the Qilin group caused significant operational disrupti...
Read More » -

Achieve SOC 2 & ISO 27001 Backup Compliance
SOC 2 and ISO 27001 require a systematic approach to data backup, treating it as verifiable proof of operational integrity and security commitments, not just disaster recovery. SOC 2 is a U.S. audit framework focused on five Trust Services Criteria, with security as mandatory, while ISO 27001 is ...
Read More » -

Why Martech Needs Quality Management to Succeed
Martech practitioners are essential for integrating quality management processes like QA and UAT, bridging marketing and IT to ensure projects meet business needs and avoid significant risks. Quality assurance focuses on technical system integrity, while user acceptance testing evaluates the cust...
Read More » -

Ransomware gang asked BBC reporter to hack media giant
A BBC cybersecurity journalist was targeted by the Medusa ransomware gang, which attempted to recruit him as an insider threat to gain network access in exchange for a share of a ransom payment. The Medusa gang is known for double-extortion tactics and has been linked to over 300 attacks on U.S. ...
Read More » -
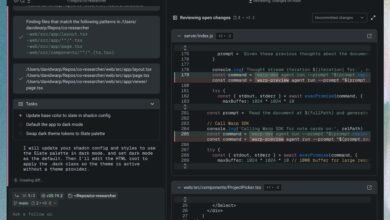
Warp Agentic: The Top Development Tool of 2025
Warp Agentic is a leading 2025 development tool that boosts productivity through integrated code generation, debugging, and project management features. It enhances team collaboration with real-time shared workspaces and reduces delays from communication and version control issues. The platform o...
Read More »