Topic: zero-day vulnerabilities
-

Apple, Google Rush Emergency 0-Day Security Patches
Apple and Google have released emergency security updates to patch actively exploited zero-day vulnerabilities, urging immediate installation to protect devices from sophisticated, targeted attacks. The coordinated response involved Apple fixing flaws in its WebKit browser engine and Google addre...
Read More » -

Microsoft Fixes 3 Actively Exploited Zero-Day Vulnerabilities
Microsoft patched three actively exploited zero-day vulnerabilities in its October 2025 Patch Tuesday, including flaws in a pre-installed modem driver, Windows Remote Access Connection Manager, and IGEL OS, requiring immediate updates. The vulnerabilities enable attackers to escalate privileges t...
Read More » -

Hackers Exploit 29 Zero-Days at Pwn2Own Automotive
The Pwn2Own Automotive 2026 hacking competition awarded nearly half a million dollars on its second day, highlighting the critical need to secure modern vehicle systems like EV chargers and infotainment units. Leading team Fuzzware.io earned $213,000, including $95,000 for exploiting zero-day fla...
Read More » -

Microsoft Patch Tuesday fixes 3 zero-days, 114 flaws in January 2026 update
Microsoft's January 2026 Patch Tuesday addresses 114 vulnerabilities, including eight critical flaws and three zero-days, with one confirmed as actively exploited. The actively exploited zero-day (CVE-2026-20805) is an information disclosure flaw in the Desktop Window Manager, while the other two...
Read More » -

Microsoft Patches 3 Zero-Days, 57 Flaws in December Update
Microsoft's December 2025 Patch Tuesday addressed 57 vulnerabilities, including three critical remote code execution flaws and three zero-day issues. One zero-day (CVE-2025-62221) is actively exploited, allowing local privilege escalation, while two others were publicly disclosed before patching....
Read More » -

AI Supply Chains at Risk from Critical PickleScan Flaws
Researchers discovered three critical zero-day vulnerabilities (CVSS 9.3) in PickleScan, a tool for inspecting Python pickle files and PyTorch models, which allow attackers to bypass security checks and distribute malicious machine learning models. The flaws include a file extension bypass, a dis...
Read More » -

Microsoft Patches 6 Zero-Day Exploits in Critical October Update
Microsoft's October 2025 Patch Tuesday addresses 172 vulnerabilities, including six actively exploited zero-days and eight critical-rated flaws, with a focus on remote code execution and privilege escalation risks. Windows 10 has reached its end of support, requiring users to enroll in Extended S...
Read More » -

Cisco ASA Firewalls Under Active Attack from Zero-Day Exploits
Cisco has issued an urgent alert to patch two actively exploited zero-day vulnerabilities (CVE-2025-20333 and CVE-2025-20362) affecting its ASA and FTD software. The company, aided by international cybersecurity agencies, also addressed a third critical flaw (CVE-2025-20363) but has not linked it...
Read More » -

Active Attacks Exploit Cisco ASA Zero-Day Flaws
A coordinated international cybersecurity alert warns of active attacks exploiting zero-day vulnerabilities in Cisco ASA and FTD software, attributed to a sophisticated, likely state-sponsored threat actor linked to previous ArcaneDoor campaigns. Two critical vulnerabilities (CVE-2025-20362 and C...
Read More » -

VMware patches critical ESXi zero-day bugs exploited at Pwn2Own
VMware released critical security updates for four vulnerabilities in ESXi, Workstation, Fusion, and Tools, originally exploited as zero-days during Pwn2Own Berlin 2025. Three high-severity flaws (CVSS 9.3) allow guest VM attackers to execute arbitrary code on the host, involving memory corruptio...
Read More » -

Windows 10 Final Patch Tuesday Fixes 6 Zero-Day Flaws
Microsoft released security updates addressing 172 vulnerabilities, including six zero-day threats, with three already actively exploited, demanding immediate action from system administrators. Three critical zero-day vulnerabilities are under active exploitation: CVE-2025-59230 in Windows Remote...
Read More » -

Urgent: FortiWeb Flaw Exploited, Logitech Breach Exposed
A critical vulnerability in FortiWeb (CVE-2025-58034) is being actively exploited due to a stealth patch that left many administrators unaware of the necessary update. Logitech confirmed a data breach affecting limited employee and customer details, while a widespread Cloudflare outage disrupted ...
Read More » -

Top 10 Cybersecurity Stories of 2025: The Year's Biggest Breaches & Threats
Major cybersecurity vendors withdrew from the MITRE ATT&CK Evaluations in 2025, citing the tests' growing complexity and shift toward marketing, prompting plans for reform ahead of the 2026 cycle. A widespread proxy network compromised thousands of vulnerable IoT devices to facilitate malicious a...
Read More » -

$3.2M Awarded for 11 Zero-Day Cloud Vulnerabilities
The inaugural Zeroday Cloud cybersecurity competition awarded over $300,000 for the discovery of 11 zero-day vulnerabilities in major cloud platforms, highlighting persistent security challenges in complex cloud environments. A critical container escape flaw in the Linux kernel was uncovered, pos...
Read More » -

Google Patches Actively Exploited Zero-Day Vulnerabilities
Google has released a critical Android security update patching over 100 vulnerabilities, including three severe flaws that are under active, targeted exploitation. Two high-severity information disclosure vulnerabilities (CVE-2025-48633 & CVE-2025-48572) can expose sensitive data or grant elevat...
Read More » -
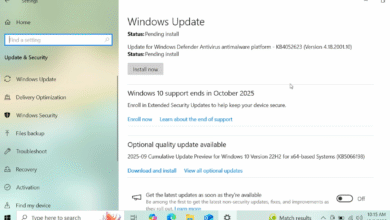
October 2025 Patch Tuesday: Final Windows 10 Updates
Microsoft's October 2025 Patch Tuesday marks the final scheduled update for Windows 10, addressing 172 security vulnerabilities including two actively exploited zero-day flaws. Critical vulnerabilities include remote code execution bugs in Microsoft Office's Preview Pane and Windows Server Update...
Read More » -

ArcaneDoor Hackers Renew Cisco Attacks with Stealthy Campaign
A sophisticated cyber-espionage campaign by the ArcaneDoor threat actor has compromised older Cisco ASA firewalls using zero-day vulnerabilities to implant malware and steal data. The attackers used advanced evasion techniques and modified the ROM Monitor to ensure persistence, but only older mod...
Read More » -

AISLE Launches AI-Powered System to Stop Zero-Day Threats
AISLE has launched an AI-native cyber reasoning system that autonomously detects, prioritizes, and fixes known and zero-day vulnerabilities, addressing the primary cause of security incidents. The platform reduces remediation time from weeks or months to days or minutes by generating ready-to-mer...
Read More » -

Synology Patches Critical BeeStation Flaws Exposed at Pwn2Own
Synology released a critical security update for BeeStation devices to fix a remote code execution vulnerability (CVE-2025-12686) caused by an unchecked buffer copy operation. The flaw was exploited live at Pwn2Own Ireland 2025, earning researchers a $40,000 prize, and users must upgrade to BeeSt...
Read More » -
Ivanti Zero-Day Breach Hits European Governments
A coordinated cyber campaign exploited vulnerabilities in Ivanti Endpoint Manager Mobile (EPMM), compromising several European government bodies including the European Commission, Finnish government, and Dutch agencies in late January. The breaches exposed sensitive work-related data like employe...
Read More » -

AI Hacking Skills Near Critical 'Inflection Point'
AI is rapidly approaching an inflection point where its ability to discover software vulnerabilities could soon surpass traditional cybersecurity defenses, creating a powerful dual-use technology. Recent breakthroughs, like simulated reasoning and agentic AI, have drastically enhanced models' cap...
Read More » -

Windows Kernel Flaw Fixed, Fortinet Zero-Day Exploited
Cybersecurity demands constant vigilance against evolving threats like zero-day exploits and requires organizations to adopt layered defense strategies that combine awareness, collaboration, and resilience. Emerging technologies are reshaping security, with innovations such as touchless Wi-Fi ent...
Read More » -

Bitdefender Launches Standalone PHASR for Proactive Endpoint Security
Bitdefender has launched GravityZone PHASR as a standalone solution, enabling businesses to add advanced pre-emptive protection to their existing security systems without replacing them. PHASR merges behavior-based security hardening with live threat intelligence to proactively block ransomware a...
Read More » -

Windows 10 Gets Final Major Update as Windows 11 Takes the Spotlight
The final major update for Windows 10 has been released, as Microsoft shifts focus to Windows 11, with official support ending next month and users needing to upgrade or enroll in extended security services. The September update includes crucial security patches addressing 81 vulnerabilities, inc...
Read More » -

Tenable Achieves PROTECTED IRAP & Hits Record Patch Tuesday
Tenable Cloud Security has achieved PROTECTED level certification under Australia's IRAP, validating its robust security controls for government cloud deployments and enabling informed risk-based decisions. The platform addresses multi-cloud security challenges by integrating security throughout ...
Read More » -

Hackers Ditch Encryption, Focus on Data Theft and Extortion
Cybercriminals are increasingly shifting from ransomware to "encryptionless" extortion, stealing and threatening to release data without locking files, which bypasses traditional defenses. The primary attack methods involve exploiting unpatched software vulnerabilities and supply chain weaknesses...
Read More » -

AI Browsers: The Looming Cybersecurity Threat
The rapid integration of AI into web browsers introduces serious cybersecurity vulnerabilities, including data breaches and privacy invasions, as these tools collect and retain more personal data than traditional browsers. Security researchers have identified flaws in early AI browsers, such as p...
Read More » -

Ex-L3Harris Cyber Chief Pleads Guilty in Russian Trade Secrets Plot
Peter Williams, a former cybersecurity director at L3Harris Trenchant, pleaded guilty to selling classified trade secrets valued at over $1 million to a Russian entity. He faces a potential prison sentence of 87 to 108 months, financial penalties up to $300,000, and $1.3 million in restitution, w...
Read More » -

Oracle Hackers Target Executives with Extortion Emails
A sophisticated hacking campaign is targeting top-level executives at major corporations with extortion emails, claiming to have stolen sensitive data from Oracle's widely used business software products, though these claims remain unverified. The attackers, linked to the Clop ransomware gang, us...
Read More » -

Oracle Ties Clop Ransomware to Critical July 2025 Flaws
Oracle has linked extortion emails from the Clop ransomware group to critical vulnerabilities in its E-Business Suite, which were patched in July 2025, urging customers to apply updates immediately. The attackers claim to have stolen sensitive data from Oracle systems and are threatening to relea...
Read More » -

Apple Issues Spyware Attack Warning to Targeted Users
Apple has issued urgent warnings about sophisticated mercenary spyware attacks targeting high-profile individuals via zero-interaction exploits. These attacks exploit zero-day vulnerabilities, often without victim interaction, and primarily target journalists, activists, politicians, and official...
Read More » -

Vulnhuntr: Find Remotely Exploitable Vulnerabilities Fast
Vulnhuntr combines static code analysis with large language models (LLMs) to detect complex, multi-step vulnerabilities that traditional scanners miss by tracking data flow across applications. The tool systematically breaks down code analysis to overcome LLM context limitations, tracing user inp...
Read More » -

Oracle Customers Warned of E-Business Suite Data Breach
Businesses using Oracle's E-Business Suite are receiving threatening emails from attackers claiming to have stolen data and demanding millions in ransoms, though these breach claims remain unverified. The campaign originated from compromised email accounts, with security experts noting possible l...
Read More » -

Palo Alto Networks Login Portals Under Massive Attack Surge
A dramatic 500% surge in suspicious network scans is targeting Palo Alto Networks login portals, with over 1,285 unique IPs involved, indicating a coordinated reconnaissance campaign. The majority of scanning IPs originated from the U.S., with clusters focusing on targets in the U.S. and Pakistan...
Read More » -

Transform Cyber Defense with Exposure Management
Effective cybersecurity requires a proactive shift to exposure management, moving beyond reactive tools to first gain complete visibility of all digital assets that could be targeted. Attackers use reconnaissance to map an organization's external presence, enabling them to exploit new vulnerabili...
Read More » -

VPN Credentials Fuel 50% of Ransomware Attacks
Ransomware activity surged in Q3 2025, with compromised VPN credentials being the primary entry point for nearly half of all breaches, driven mainly by three groups: Akira, Qilin, and INC Ransomware. The Akira group specifically targeted SonicWall appliances using credential stuffing attacks, exp...
Read More » -

France Alerts Apple Users to Major New Spyware Threat
French cybersecurity authorities have issued urgent warnings to Apple users about a major new spyware threat, following alerts from Apple indicating potential device compromise. Affected users are advised to contact CERT-FR immediately, preserve Apple's notification email, and avoid altering thei...
Read More » -

Microsoft Fixes 59 Flaws, 6 Already Under Attack
Microsoft has patched 59 vulnerabilities, with six actively exploited flaws requiring urgent updates to prevent breaches. The exploited vulnerabilities include security bypasses and privilege escalations, which can allow attackers to disable security tools or compromise networks. Microsoft is als...
Read More » -

5-Year-Old FortiOS 2FA Flaw Actively Exploited, Fortinet Warns
A critical 2020 Fortinet FortiGate firewall vulnerability (CVE-2020-12812) is still being actively exploited, allowing attackers to bypass two-factor authentication by manipulating username case during login. Despite patches being available for over five years, exploitation continues, particularl...
Read More » -

Thousands of FortiCloud SSO Devices Vulnerable to Remote Hacks
Tens of thousands of internet-facing Fortinet devices remain vulnerable to critical authentication bypass flaws (CVE-2025-59718/9), creating a massive attack surface that is already under active exploitation. Attackers exploit the flaw using crafted SAML messages to gain administrative access, al...
Read More » -

Google Patches Actively Exploited Chrome Zero-Day Vulnerability
Google has issued an urgent update for Chrome to fix a critical zero-day vulnerability (CVE-2025-13223) that is actively being exploited, requiring immediate user action to prevent data breaches. The vulnerability is a type confusion flaw in the V8 engine that attackers can exploit via malicious ...
Read More » -

New Gladinet Triofox Flaw Exploited by Attackers (CVE-2025-12480)
A critical security flaw (CVE-2025-12480) in Gladinet Triofox allows unauthenticated attackers to bypass access controls and gain administrative privileges, which has been exploited by the threat group UNC6485 since late August 2025. Attackers used an HTTP Host header attack to access the configu...
Read More » -

Bitdefender & CYPFER: End-to-End Cyber Resilience for Businesses
Bitdefender and CYPFER have partnered to provide end-to-end cyber resilience, integrating incident response, forensic investigation, and rapid recovery into Bitdefender's security portfolio for businesses of all sizes. The collaboration combines Bitdefender's threat detection and intelligence wit...
Read More » -

Palo Alto Portal Scans Skyrocket 500%
GreyNoise reported a 500% surge in reconnaissance scans targeting Palo Alto Networks login interfaces, with 1,300 distinct IPs detected on October 3rd, primarily originating from the United States. Similar scanning campaigns have targeted other remote access services like Cisco ASA, with shared c...
Read More »