Topic: file encryption
-

ShinyHunters Unleash ShinySp1d3r Ransomware-as-a-Service
A new ransomware-as-a-service platform called ShinySp1d3r is being developed by threat actors linked to ShinyHunters and Scattered Spider, marking a strategic shift from using established gangs' encryptors to building their own bespoke operation. The ransomware features advanced capabilities incl...
Read More » -

Identify Ransomware: .BAGAJAI Ext (MedusaLocker3/Far Attack)
The .BAGAJAI ransomware encrypts files and targets backups, demanding a ransom via specific TOR pages or email addresses, posing a severe threat to small businesses and individuals. Security analysis uncovered malicious components like chisel.exe and BAGAJAI.exe, along with Mimikatz tools, indica...
Read More » -

Identify & Remove .BAGAJAI Ransomware (MedusaLocker3)
The .BAGAJAI ransomware, a variant of MedusaLocker3, encrypts files and demands cryptocurrency payment for decryption, often leaving victims with compromised backups and no free recovery tools available. Attackers use sophisticated methods like credential dumping tools such as Mimikatz to escalat...
Read More » -
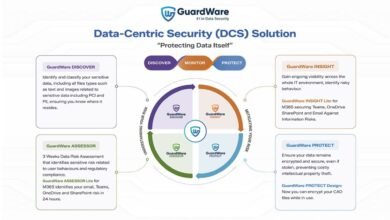
GuardWare Launches World-First Solution to Permanently Stop Data Theft
GuardWare has launched PROTECT, a pioneering encryption software suite that persistently secures sensitive data during active use, enabling secure movement in supply chains and remote file destruction. PROTECT addresses vulnerabilities in unstructured data files by employing a data-centric securi...
Read More » -

Akira Ransomware Hijacks Victim's Remote Management Tool
Hackers used the trusted Datto RMM tool and a Living Off The Land strategy to deploy Akira ransomware, disguising their actions as normal IT operations to avoid detection. The attack was halted by Barracuda Managed XDR, which detected the encryption activity and immediately isolated the compromis...
Read More » -

Unmasking the .54lg9 File Extension: Mimic/Pay2Key Threat Explained
A server migration failure due to neglected backup protocols allowed ransomware to enter through an unprotected workstation, encrypting files with a .54lg9 extension and halting operations. The ransomware, suspected to be from the Pay2Key family, spread despite Bitdefender on most machines, and n...
Read More » -

Unlocking the .54lg9 File Extension: What You Need to Know
The .54lg9 file extension indicates a ransomware infection that can encrypt files on the infected device and spread across networks, complicating recovery. Without reliable backups, restoration options are limited; paying the ransom is discouraged, and instead, isolation, professional help, and r...
Read More » -

New Lockbit 3.0 Ransomware Uses .G5xG4GUv2 Extension
A car repair shop experienced a ransomware attack that encrypted files and disrupted operations, emphasizing the need for strong backups and updated security. The attack exploited outdated software and weak network credentials, spreading to shared folders and leaving a ransom note with a unique f...
Read More » -

ESET Uncovers "PromptLock" AI-Driven Ransomware Threat
Slovakia-based cyber security vendor ESET said it has discovered "the first known" artificial intelligence-powered ransomware that generates malicious scripts on-the-fly on infected machines. ESET called the ransomware "PromptLock", and has uploaded Microsoft Windows and Linux samples to Google's VirusTotal scanning site. PromptLock accesses the Apache-licensed open source GPT-OSS:20b AI model from OpenAI via the Ollama API to generate scripts written in the Lua language. Lua scripts used by Pro...
Read More » -

AI-Powered PromptLock Ransomware Encrypts and Steals Data
A new AI-driven ransomware named PromptLock has been identified, using Lua scripts to encrypt and steal data across Windows, macOS, and Linux systems, marking a significant evolution in cyber threats. The malware leverages OpenAI's gpt-oss:20b model via the Ollama API to generate malicious script...
Read More » -

ELENOR-Crop Ransomware: Mimic & Pay2Key Threat Analysis
The ELENOR-Crop ransomware uses advanced encryption to lock victims out of their data and demands payment for decryption keys, requiring an understanding of its behavior for effective mitigation. Attackers communicate via a specific email, use misleadingly friendly messages to pressure victims in...
Read More » -

Files Encrypted with .rgPrGzyZY Extension
Files encrypted with the .rgPrGzyZY extension indicate a severe ransomware attack, locking data until a ransom is paid, though experts discourage compliance. Attackers exploit IT vulnerabilities, exfiltrating sensitive data like financial records and threatening leaks unless paid. Cybersecurity p...
Read More »