Topic: dll sideloading
-

LinkedIn Phishing Attack Uses Pen Testing Tool to Target Executives
A sophisticated phishing campaign targets business leaders and IT professionals via LinkedIn, using industry-specific lures to build false trust and deliver malicious links. The attack deploys a Remote Access Trojan (RAT) by abusing a legitimate PDF reader through DLL sideloading, which complicat...
Read More » -

EDR Exploited for Stealthy Ransomware Attacks
Attackers are exploiting trusted security tools like EDR software and Windows utilities to deploy malware with stealth and persistence, shifting from mass phishing to more sophisticated methods. A specific attack involved social engineering to execute malicious commands, sideloading a rogue DLL v...
Read More » -

North Korean Lazarus Hackers Target European Defense Firms
North Korea's Lazarus hacking group targeted European UAV defense firms through a deceptive recruitment campaign called Operation DreamJob, aiming to steal military drone technology. The attackers used trojanized applications and DLL sideloading to deploy the ScoringMathTea RAT, granting extensiv...
Read More » -
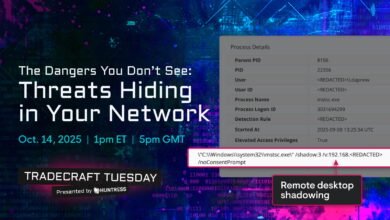
Inside the PureRAT Attack: From Info Stealer to Full Control
A sophisticated cyberattack begins with phishing emails using sideloading techniques to deploy malware, escalating from credential theft to deploying the full-featured PureRAT remote access trojan for complete system control. The campaign employs multiple layers of obfuscation, including custom c...
Read More » -

China's Salt Typhoon Hackers Target European Telecoms
A China-linked cyber espionage group known as Salt Typhoon is targeting European telecommunications providers to infiltrate critical infrastructure for intelligence gathering and surveillance. The attackers exploited a Citrix NetScaler Gateway vulnerability, deployed the SNAPPYBEE backdoor via DL...
Read More » -

From ClickFix to MetaStealer: How Cyber Threats Are Evolving
Cybersecurity attacks are evolving with threat actors combining social engineering and technical methods, such as using disguised installers and legitimate tools to deploy malware like MetaStealer. Recent incidents involve deceptive techniques, including fake verification pages and malicious file...
Read More »