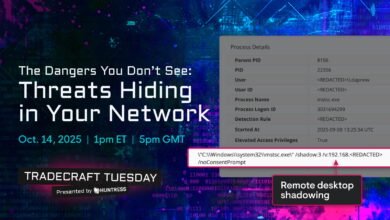
Topic: defense evasion
-

Inside the PureRAT Attack: From Info Stealer to Full Control
A sophisticated cyberattack begins with phishing emails using sideloading techniques to deploy malware, escalating from credential theft to deploying the full-featured PureRAT remote access trojan for complete system control. The campaign employs multiple layers of obfuscation, including custom c...
Read More »