Topic: threat attribution
-

CISA Alerts: Chinese "BrickStorm" Malware Targets VMware Servers
A sophisticated Chinese-linked malware campaign called "Brickstorm" is targeting VMware vSphere servers, using hidden virtual machines to steal credentials and compromise networks, as detailed by U.S. and Canadian cybersecurity agencies. The malware employs advanced evasion techniques like encryp...
Read More » -
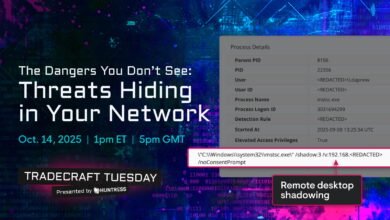
Inside the PureRAT Attack: From Info Stealer to Full Control
A sophisticated cyberattack begins with phishing emails using sideloading techniques to deploy malware, escalating from credential theft to deploying the full-featured PureRAT remote access trojan for complete system control. The campaign employs multiple layers of obfuscation, including custom c...
Read More » -

New MacOS Malware 'DigitStealer' Targets Apple M2/M3 Chips
DigitStealer is a sophisticated malware targeting macOS systems with Apple M2 and M3 chips, disguising itself as legitimate tools like DynamicLake or Google Drive to trick users into installation. The malware employs a multi-stage delivery process, checking system location and hardware to avoid v...
Read More » -

FlexibleFerret Malware Strikes macOS With Go Backdoor
A sophisticated malware campaign named FlexibleFerret targets macOS systems using a multi-stage attack to bypass security, deploy a persistent backdoor, and steal sensitive credentials through deceptive applications. The attack begins with a shell script that identifies the system architecture, d...
Read More » -

Oracle Customers Warned of E-Business Suite Data Breach
Businesses using Oracle's E-Business Suite are receiving threatening emails from attackers claiming to have stolen data and demanding millions in ransoms, though these breach claims remain unverified. The campaign originated from compromised email accounts, with security experts noting possible l...
Read More » -

CISA Urges Immediate Patch for Samsung Spyware Zero-Day
A critical vulnerability (CVE-2025-21042) in Samsung smartphones allows attackers to install LandFall spyware via manipulated DNG images sent through WhatsApp, affecting Android 13 and newer devices. The spyware, exploited since July 2024, can steal sensitive data like contacts, messages, and loc...
Read More » -

CPU Spike Exposed RansomHub Ransomware Attack
An employee inadvertently triggered a ransomware attack by downloading a malicious file disguised as a browser update, initiating automated reconnaissance and credential harvesting. Attackers established persistence and network access through a SOCKS proxy, exploiting Active Directory weaknesses ...
Read More » -

New Salty2FA Phishing Kit Raises Sophistication Alarm
The Salty2FA phishing kit uses advanced tactics like session-based subdomain rotation, legitimate platform abuse, and precise corporate branding to create highly convincing fraudulent login pages. It incorporates Cloudflare’s Turnstile and obfuscated JavaScript to evade automated analysis and com...
Read More » -

Sedgwick Subsidiary Breach Exposes Government Contractor Data
A data breach at Sedgwick Government Solutions exposed sensitive information from over twenty federal agency clients, including CISA, DHS, and CBP, though the parent company's core network was unaffected. The breach was isolated to a file transfer system, with no evidence of access to primary cla...
Read More »