Exposure Management: The New Boardroom Test
▼ Summary
– Cybersecurity has become a boardroom issue with regulatory, investor, and reputational risks, not just a technical concern for CISOs.
– Exposure management bridges the gap by identifying and prioritizing exposures that could cause material harm, providing a quantifiable view of risk.
– Organizations progress through five maturity stages, from reactive and siloed security to optimized, business-aligned risk management.
– Boards must demand metrics on exposure threats and progress, moving beyond traditional measures like patches applied or alerts closed.
– Achieving cyber maturity requires honest assessment, unifying teams, breaking down silos, and embedding business context into risk decisions.
Cybersecurity has firmly moved from the server room to the boardroom, demanding executive attention amid growing regulatory pressure, investor concerns, and serious reputational threats. Despite massive financial investments in security infrastructure, data breaches continue to escalate. This troubling gap doesn’t stem from insufficient funding but from a fundamental failure to grasp the complete picture and communicate it effectively to company leadership. Exposure management provides the critical framework needed to close this divide.
Rather than judging effectiveness by counting resolved alerts or installed patches, this approach focuses on continuously discovering, ranking, and eliminating the exposures posing the greatest potential for significant business damage. When properly implemented, it delivers precisely what modern boards require: a measurable, business-centric perspective on both operational and cyber risk that strengthens governance and bolsters investor trust.
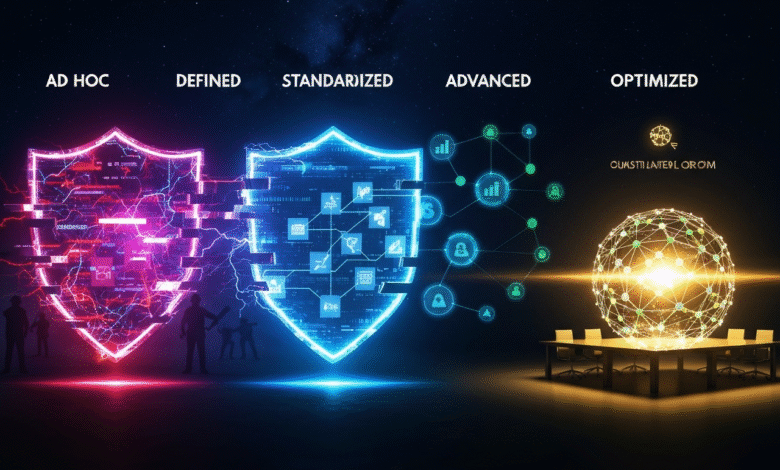
Companies worldwide exhibit five clearly defined levels of maturity in their exposure management programs. Organizations at the lower end operate with fragmented security functions and teams that fail to grasp the interconnected vulnerabilities attackers leverage. Their attention stays fixed on individual security findings, rendering these less mature programs highly inefficient. At the opposite extreme, mature organizations consolidate their security data, enrich it with contextual insights about asset and identity relationships, and concentrate on exposure to filter out irrelevant noise. Pinpointing your company’s present standing is essential, as it maps out a definitive improvement trajectory and ultimately decides whether you attain cyber resilience or confront substantial liabilities.
Stage 1: Ad Hoc
This initial phase involves limited tools that scan only small segments of the attack surface. Procedures are purely reactive, personnel rush to address emerging threats, and prioritization amounts to little more than guesswork. Board members observe spending that lacks any coherent strategy, leaving the organization in a constant state of vulnerability.
Stage 2: Defined
Basic security tools and frameworks are established. Staff receive formal assignments, processes are documented, and risk assessments expand in scope. While this marks an improvement, the setup remains fragile. Risks continue to exist in isolation, reporting lacks cohesion, and a single security incident can still cause widespread operational disruption.
Stage 3: Standardized
Superficially, maturity appears robust: security tools encompass the entire attack surface, procedures are uniform, and business context starts influencing risk decisions. Many firms become stuck at this plateau. Dashboards may indicate advancement, but the absence of comprehensive visibility creates dangerous blind spots, particularly when adversaries link multiple exposures across different domains.
Stage 4: Advanced
This represents a pivotal transition point. Asset and risk information consolidates into a unified inventory. Risk scoring becomes standardized. Prioritization now integrates both technical severity and business impact. Organizations at this stage start identifying not just standalone vulnerabilities, but dangerous combinations, like a misconfigured cloud workload coupled with an over-privileged user account, that form genuine attack pathways to critical assets. Exposure management transforms from descriptive to predictive.
Stage 5: Optimized
This is the ultimate objective. Exposure management aligns completely with business goals. Metrics remain consistent across all domains. Reporting becomes quantifiable, comparable, and directly linked to business consequences. Remediation efforts, resource allocation, and investment choices all follow clearly defined risk objectives. At this peak stage, cybersecurity evolves from a cost center into a strategic driver enabling business growth, customer trust, and organizational resilience.
Why should boards care about this maturity curve?
Corporate directors cannot risk complacency, especially with intensified regulatory scrutiny and compliance demands. Watchdog agencies are monitoring closely, investors pose increasingly difficult questions, and cyber insurance premiums continue climbing. Exposure Management empowers boards and their organizations to demonstrate tangible, real-time progress and success metrics to both shareholders and regulators.
Nevertheless, a large number of companies remain stalled at stages two or three. They possess frameworks and technologies, but without unified visibility and contextual understanding, they cannot prioritize remediation efforts intelligently. Boards must insist on clear answers to crucial questions: “Which exposures genuinely endanger our business?” “What verifiable progress are we achieving in mitigating them?” “How does our maturity level compare to industry competitors?” Outdated metrics like “patched vulnerabilities” or “closed alerts” no longer provide adequate insight.
Navigating the path forward – Starting points and progression strategies
Advancing along the cyber maturity curve is not an instantaneous process. It commences with a candid evaluation to determine the organization’s current position and the target level needed to meet governance requirements. Although tools and frameworks play important roles, genuine advancement originates from unifying teams, dismantling departmental silos, and embedding business context into every risk-related decision.
Exposure management transcends being merely another technology buzzword. It constitutes a disciplined practice that determines whether an organization merely responds to emergencies or proactively prevents them. For corporate boards, achieving maturity is no longer an optional consideration. It represents a core accountability. For businesses themselves, it equates to survival, and it can be accomplished without invalidating previous technology investments.
(Source: ITWire Australia)
