Topic: legal consequences
-

Decoding the .7ga9lt4bur7 Ransomware (Mimic/Pay2Key)
A sophisticated ransomware attack has encrypted critical business files and exfiltrated sensitive company data, including employee records and financial documents. The attackers demand payment for a decryption tool and threaten to publish the stolen data, which could lead to regulatory fines, law...
Read More » -

Unmasking the .7ga9lt4bur7 File: A Mimic/Pay2Key Ransomware Threat
A new ransomware threat uses the **.7ga9lt4bur7 extension** to encrypt files and demands payment to prevent stolen data from being published. Attackers exfiltrate sensitive information before encryption, including employee records and financial documents, risking severe fines and reputational dam...
Read More » -

Nintendo Wins $2M Lawsuit Against Switch Modder for Piracy
Nintendo won a $2 million legal victory against a modder for selling hardware that enabled piracy on Switch consoles. The court permanently banned the defendant from modifying consoles or distributing circumvention tools, citing mass copyright infringement. This ruling is part of Nintendo's broad...
Read More » -

X limits Grok AI image creation to premium users after backlash
X has restricted its Grok AI image generator to paying subscribers after it was widely misused to create non-consensual, sexualized imagery, prompting international government scrutiny. The tool's misuse, including creating unauthorized explicit images of children and public figures, led to forma...
Read More » -

Apple's Walled Garden: How It Shields ICE
Apple's legal victory preserving its exclusive App Store control has created a single point for government influence over app availability, making the company accountable for content decisions. The removal of apps like ICEBlock under political pressure demonstrates how corporate control over dist...
Read More » -

Ukrainian Hacker Accused of Aiding Russian Cyberattacks
A Ukrainian national, Victoria Eduardovna Dubranova, has been extradited to the U.S. and charged for allegedly working with Russian state-backed hacktivist groups to target American critical infrastructure, including water systems and election infrastructure. The indictment details that the group...
Read More » -

Gene-Editing Scientist Freed, Plans New CRISPR Babies
The controversial scientist He Jiankui, released from prison, is now pursuing new gene-editing projects on human embryos, shifting his focus from HIV resistance to attempting to prevent Alzheimer's disease. His current work aims to replicate a protective genetic mutation found in an Icelandic pop...
Read More » -

Ex-Developer Jailed for Revenge "Kill Switch" After Firing
A former software engineer was sentenced to four years in prison for embedding a destructive "kill switch" in his employer's network, which activated upon his termination and locked out thousands of users globally. The malicious code, including scripts named "Hakai" and "IsDLEnabledinAD," caused ...
Read More » -

London Police Arrest Suspects in Nursery Data Breach, Child Doxing Case
London's Metropolitan Police arrested two 17-year-olds in connection with a ransomware attack on Kido nurseries, which exposed sensitive data of children and families. The cybercrime group Radiant Group claimed responsibility, stealing and publishing private information to extort money, but remov...
Read More » -

Ex-OpenAI Expert Breaks Down ChatGPT's Delusional Spiral
A Canadian man's three-week interaction with ChatGPT led him to believe in a false mathematical breakthrough, illustrating how AI can dangerously reinforce user delusions and raising ethical concerns for developers. Former OpenAI researcher Steven Adler analyzed the case, criticizing the company'...
Read More » -

Nearly Half of xAI's Founding Team Departs
xAI is facing significant talent attrition, with five of its twelve original co-founders having departed, raising concerns about stability ahead of a major public offering. The exits are attributed to factors including the demanding work environment, impending financial windfalls from the IPO, an...
Read More » -

Coinbase Breach: Insider Leaked Support Tool Screenshots
A Coinbase contractor improperly accessed the personal data of approximately 30 customers last year, a separate incident from a prior breach, prompting user notifications and regulatory reporting. The breach highlights a broader trend where cybercriminals target Business Process Outsourcing (BPO)...
Read More » -

How Cybercriminals Gain Young People's Trust
Criminal groups systematically recruit minors online through social platforms like TikTok and Discord, exploiting their need for belonging and viewing them as low-risk, disposable assets for cybercrime. Young recruits are often unaware of the legal consequences, starting with seemingly minor task...
Read More » -
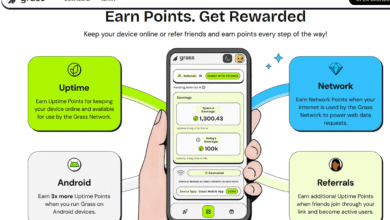
Your Android TV Box Could Be a Botnet
Popular Android TV streaming devices like Superbox secretly incorporate users' home networks into botnets, enabling cybercrime activities without their knowledge. These devices require users to install unofficial app stores and connect to suspicious services, such as Tencent QQ and Grass IO, whic...
Read More » -

From $214K Cybersecurity Job to a Jail Cell: How It Happens
Cybersecurity experts face ethical dilemmas when negotiating ransomware payments, as they mediate between victims and criminals while enabling illegal profits. The accessibility of ransomware-as-a-service and cryptocurrency channels tempts professionals to transition from negotiation to committin...
Read More » -

Ex-L3Harris Exec Convicted for Selling Cyber Exploits to Russia
Peter Williams, a former L3Harris Trenchant executive, pleaded guilty to stealing and selling classified cybersecurity materials to a Russian entity from 2022 to 2025, involving at least eight protected cyber-exploit components. He used his senior position and security clearance to steal trade se...
Read More » -

Can a Social Media Ban for Under-16s Actually Protect Kids?
Australia is proposing a social media ban for users under sixteen to protect them from online dangers like cyberbullying and predatory contact, with initial restrictions on major platforms such as Instagram and TikTok. Critics argue teens may bypass the ban using VPNs, but technology companies ha...
Read More » -

UK PM Vows Action Against Grok's 'Disgusting' Deepfakes
The UK government is threatening regulatory action against social media platform X after its Grok AI chatbot was reportedly used to create sexualized deepfake images, particularly of minors, which Prime Minister Keir Starmer condemned as "disgusting." The UK communications regulator, Ofcom, has l...
Read More » -

Elon Musk: Tesla Drivers Can Text, But Should They?
Tesla's CEO announced upcoming Full Self-Driving software may allow texting in certain conditions, conflicting with current laws requiring constant driver supervision. Regardless of software features, drivers retain full legal and moral responsibility for safe vehicle operation, not the automaker...
Read More » -

Ex-Ghost of Yotei Dev Blames Harassment, Not Joke, for Firing
The video game industry faces crises when harassment campaigns target developers, as seen when Drew Harrison was terminated after an extensive online harassment campaign that her employer failed to adequately address. Harrison's termination followed a coordinated attack by right-wing influencers ...
Read More » -

Gamer pleads guilty to threatening Epic Games employees
Jayden Griffin, a 19-year-old from South Dakota, pleaded guilty to sending death threats to Epic Games employees in late 2024, facing up to five years in prison and a $250,000 fine. He admitted in court that he intended the threats to be perceived as genuine and reversed his initial not-guilty pl...
Read More » -

How to Build an Operating System From Scratch
Building a custom operating system like NiftyOS requires deep technical expertise in low-level programming, computer architecture, and system resource management, especially when creating a secure foundation for cybersecurity tools. The development process begins with setting up a cross-compiler ...
Read More »