1 Year After CrowdStrike Outage: Key Security Lessons for Enterprises
▼ Summary
– The July 19, 2024, CrowdStrike outage, caused by a faulty update, crashed 8.5 million Windows systems globally, resulting in $5.4 billion losses for top U.S. companies.
– CrowdStrike’s root cause analysis revealed fundamental quality control gaps, including missing runtime checks and logic errors, highlighting systemic failures.
– CrowdStrike implemented a Resilient by Design framework with features like Sensor Self-Recovery and a new Content Distribution System to enhance resilience.
– The incident spurred industry-wide changes, including stricter vendor evaluations and a focus on layered defenses and automatic rollback mechanisms.
– CrowdStrike’s leadership emphasized accountability and transformation, with initiatives like hiring a Chief Resilience Officer and collaborating with Microsoft.
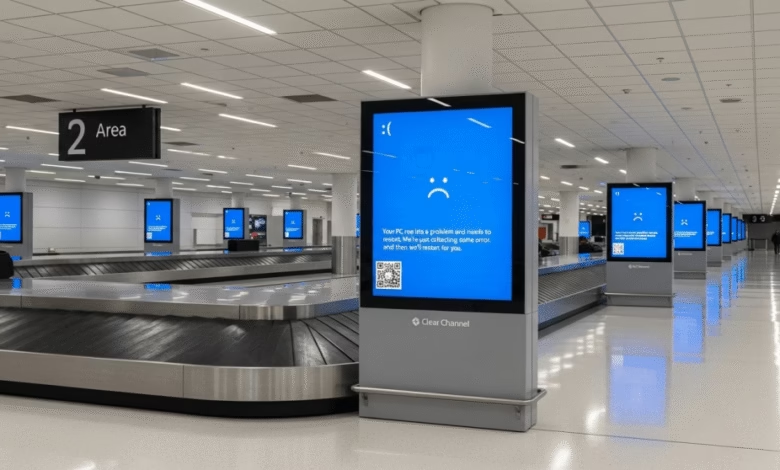
The CrowdStrike outage of July 2024 remains etched in the minds of security leaders as a stark lesson in digital fragility. What started as a routine software update triggered a global meltdown, highlighting how a single misstep inside even the strongest security architecture can ripple across industries. A year on, the fallout continues to steer how companies think about vendor risk, resilience, and system safeguards.
The sheer scale of the impact still stuns: 8.5 million Windows systems crashed in just 78 minutes, inflicting billions in losses. Airlines, banks, and hospitals all felt the blow, a clear reminder that no sector is shielded from an internal failure gone wrong. Steffen Schreier of Telesign put it bluntly: “This wasn’t a breach or an attack, just one internal failure with global consequences.” The incident forced executives to confront the uncomfortable truth that speed and convenience amplify risks when guardrails fail.
CrowdStrike’s post-mortem pulled back the curtain on gaps in quality control, missing runtime checks, flawed validation logic, and absent incremental rollouts all contributed. Merritt Baer, a veteran security expert, said better CI/CD hygiene could have softened the blow: “Had the update been rolled out incrementally, the fallout would’ve been far less severe.”
Despite the chaos, CrowdStrike won respect for its transparency. CEO George Kurtz owned the crisis in real time, which helped restore trust during recovery. The company’s response pivoted on its Resilient by Design initiative, a top-to-bottom rethink of its security setup. Among the headline upgrades: a Sensor Self-Recovery feature to stop crash loops before they cascade.
The outage did more than expose technical flaws; it sparked a wider industry reset. Vendors now face sharper scrutiny as critical supply chain partners, with CISOs demanding evidence of solid safeguards. Sam Curry of Zscaler noted that the conversation shifted from blame to resilience, pushing safer deployment practices throughout the ecosystem.
Today, AI and automation play a bigger role in risk reduction. CrowdStrike is testing autonomous systems and deepening ties with Microsoft to bake in more safeguards. The appointment of a Chief Resilience Officer signals that resilience is now a permanent priority, not a checkbox on a compliance list.
The legacy of those 78 minutes is clear: staged rollouts, manual overrides, and fallback plans are no longer nice-to-haves. As Mike Sentonas of CrowdStrike put it, “Resilience isn’t a milestone, it’s a discipline.” That discipline, forged in a global outage, now shapes how the digital world defends its foundations.
Meta Title: CrowdStrike Outage Redefined Cyber Resilience
Meta Description: The 2024 CrowdStrike outage crashed millions of systems in 78 minutes. A year later, its lessons shape how companies tackle risk and resilience.
(Source: VentureBeat)





