Fake Windows BSOD Screens Deliver ClickFix Malware
▼ Summary
– A new social engineering campaign called “PHALT#BLYX” targets the European hospitality sector with phishing emails impersonating Booking.com cancellations.
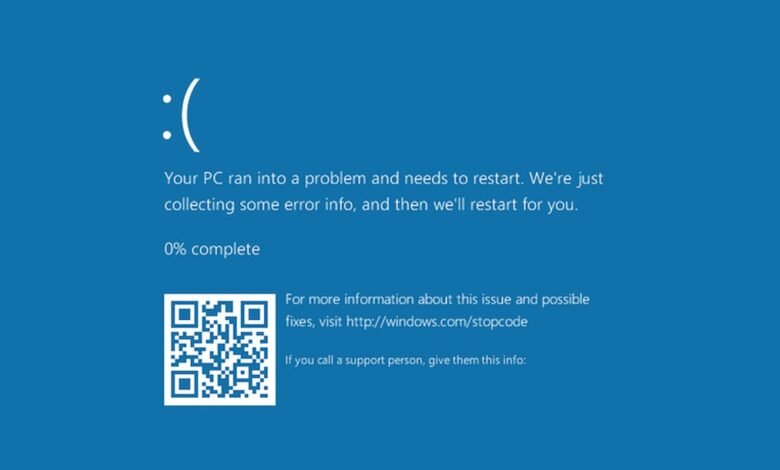
– The attack uses a fake Booking.com website that displays a fraudulent Windows Blue Screen of Death (BSOD) error to trick users.
– Victims are socially engineered to manually paste and run a malicious PowerShell command from their clipboard, infecting their own machines.
– The executed command downloads and compiles a .NET project that deploys DCRAT, a remote access Trojan, which gains persistence and system control.
– This malware provides attackers with remote desktop access, keylogging, and the ability to execute further payloads, such as a cryptocurrency miner.
A sophisticated social engineering campaign is actively targeting the European hospitality industry, using convincing fake Windows Blue Screen of Death (BSOD) screens to manipulate users into installing malware themselves. This “ClickFix” scheme begins with phishing emails that impersonate Booking.com, creating a false sense of urgency around a significant reservation cancellation and refund. The ultimate goal is to deploy a powerful remote access trojan, giving attackers a dangerous foothold within business networks.
The attack chain is carefully designed to exploit human error. After clicking a link in the deceptive email, victims are taken to a remarkably realistic clone of the Booking.com website. This fake site uses official branding and colors, making it very difficult to distinguish from the legitimate portal. It then displays a “Loading is taking too long” error, prompting the user to click for a refresh. This action triggers the core of the scam: the browser switches to full-screen mode and presents a fake Windows BSOD crash screen.
Unlike a genuine system crash, this fraudulent screen provides specific recovery instructions. It directs the user to open the Windows Run dialog, paste a command from their clipboard, and execute it. For staff under pressure or less technically experienced, the urgency of resolving a perceived system error can override suspicion. Executing this command is the critical moment of infection, as it launches a malicious PowerShell script.
The script performs a multi-stage attack. It first opens a decoy Booking.com admin page as a distraction. Meanwhile, in the background, it downloads a malicious .NET project and uses the legitimate Windows MSBuild.exe compiler to build it. The resulting payload, identified as the DCRAT remote access trojan, then works to secure its position. It adds exclusions to Windows Defender, attempts to gain administrative rights, and establishes persistence by placing a file in the system’s Startup folder.
The malware employs a technique called process hollowing, injecting its code into the legitimate `aspnet_compiler.exe` process to run stealthily in memory. Once active, it contacts a command-and-control server, transmits a full fingerprint of the infected system, and awaits instructions. DCRAT provides attackers with extensive remote control, including capabilities for remote desktop access, keylogging, launching reverse shells, and executing additional payloads directly in memory. In one observed case, the attackers used this access to install a cryptocurrency miner.
This campaign represents a significant threat because it bypasses many technical safeguards by relying on user interaction. The combination of a high-pressure phishing pretext, a flawless fake website, and a familiar-looking system error creates a powerful trap. Once the malware is installed, attackers gain a persistent presence on the network, enabling them to move laterally, steal sensitive data, and deploy further malicious tools.
(Source: Bleeping Computer)





