OpenClaw Scanner: Detect AI Agents with Open-Source Tool
▼ Summary
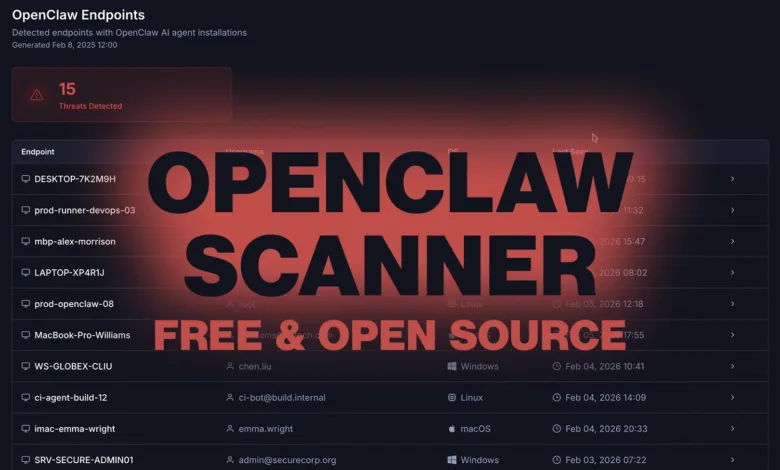
– A new free tool called OpenClaw Scanner helps organizations detect the autonomous AI agent OpenClaw (MoltBot) operating in their environments.
– The OpenClaw AI agent can perform user tasks, access local files, and authenticate to internal systems like Salesforce and Slack without centralized control.
– Security researchers have found that many OpenClaw deployments are misconfigured, exposing API keys and credentials to internal systems.
– The scanner works by analyzing existing endpoint security logs in a read-only manner, without installing new software or sending data externally.
– The tool is available for free on PyPI, and its developer, Astrix Security, plans future enhancements based on adoption and demand.
A new open-source utility has emerged, providing companies with a method to identify the presence of autonomous AI agents within their networks. The OpenClaw Scanner is a free tool designed to locate instances of the OpenClaw AI assistant, sometimes referred to as MoltBot. This particular agent can autonomously perform tasks, interact with local files, and log into internal systems, often operating without centralized management or visibility.
The OpenClaw software has seen increased adoption in recent months. It functions as an active AI agent that executes commands on a user’s behalf. The system can operate on local machines or within cloud environments, typically using common messaging applications as its control interface. Its autonomous decision-making engine allows it to carry out complex operations across various connected services and platforms.
Security investigations have revealed that numerous OpenClaw deployments suffer from significant configuration issues. Researchers have identified multiple cases where improperly set up instances could inadvertently leak sensitive data. These vulnerabilities have exposed API keys, cloud service credentials, and unauthorized access pathways to critical business systems including Salesforce, GitHub, and Slack.
The scanning tool itself is engineered to work passively within an organization’s existing security framework. It operates by analyzing behavioral data already collected by endpoint detection and response (EDR) systems, requiring only read-only access to this telemetry. The scanner does not install any new software agents on endpoints nor does it send information to external servers. This design philosophy ensures it can integrate with current security protocols without introducing new code or potential attack vectors into monitored environments.
Technically, the scanner runs as a local script that processes data exported from major EDR platforms such as CrowdStrike Falcon or Microsoft Defender for Endpoint. After analysis, it generates self-contained reports that stay entirely within the organization’s digital perimeter. These reports provide actionable context, detailing which specific devices and user accounts showed indicators of OpenClaw-related activity.
Security professionals emphasize the tool’s enterprise-focused design. “This scanner was built specifically for large organizations that need a safe, read-only method,” explained Ofek Amir, VP of R&D at Astrix Security. “It works directly over existing EDR log data without executing code on endpoints or requiring data to leave the corporate network.”
The development team at Astrix Security intends to evolve the tool’s functionality in response to user feedback and wider adoption. Planned future enhancements may include support for additional EDR platforms like SentinelOne and the ability to detect other autonomous agent frameworks that pose similar security challenges. The core scanner is currently available for installation at no cost through the Python Package Index (PyPI).
(Source: HelpNet Security)





