
- The Beginnings (1970s-1980s)
- The Evolution (1990s)
- The Diversification (2000s)
- Modern Era (2010s-Present)
- Current Landscape
- What You Need To Know?
Computer viruses are malicious programs that replicate and spread by attaching themselves to other software or files. These digital parasites have been a significant concern in computing since their inception.
The impact of viruses on digital security has been substantial. They can corrupt or delete data, steal sensitive information, and disrupt system operations. The financial toll of virus outbreaks has reached billions of dollars globally, affecting individuals, businesses, and governments alike.
Viruses exploit vulnerabilities in software and human behavior to propagate. They often spread through email attachments, infected websites, or removable storage devices. As our reliance on digital technology has grown, so has the potential for virus-related damage.
The presence of viruses has spurred the development of antivirus software and other security measures. This has led to an ongoing technological arms race between virus creators and security experts.
Understanding viruses is crucial for anyone using computers or digital devices. Awareness of how viruses operate and spread can help users protect themselves and their data from these digital threats.
The Beginnings (1970s-1980s)
The concept of self-replicating programs emerged in the early days of computing. John von Neumann, a mathematician and computer scientist, proposed the idea of self-replicating automata in the 1940s. This theoretical work laid the foundation for what would become computer viruses.
The first program resembling a virus appeared in 1971. Named Creeper, it was an experimental self-replicating program that spread through the ARPANET, the precursor to the internet. Creeper wasn’t malicious; it simply displayed the message “I’m the creeper: catch me if you can!”
The first virus to spread outside a lab environment was Elk Cloner in 1982. Written by a 15-year-old high school student, it infected Apple II computers via floppy disks. Elk Cloner would display a short poem on infected machines every 50th boot.

1986 marked a significant milestone with the emergence of Brain, the first virus to target personal computers running MS-DOS. Created by two brothers in Pakistan, Brain was designed to track illegal copies of medical software they had written. It spread rapidly, becoming the first PC virus to gain widespread attention.
These early viruses were relatively simple and often more of a nuisance than a serious threat. They primarily spread through physical media like floppy disks, limiting their reach. However, they set the stage for more complex and harmful viruses to come.
The late 1980s saw an increase in virus creation and spread. This period also witnessed the birth of the antivirus industry, as the need for protection against these digital threats became apparent.
The Evolution (1990s)

The 1990s saw rapid advancements in virus technology and a significant increase in their prevalence.
Macro viruses emerged as a major threat during this decade. In 1995, the Concept virus appeared, targeting Microsoft Word documents. It spread by infecting Word’s normal template, ensuring that every document created afterward would carry the virus. Concept demonstrated how viruses could exploit widely-used software applications.
The Melissa virus struck in 1999, combining macro capabilities with email spreading techniques. It infected a Word document and used Microsoft Outlook to send itself to the first 50 contacts in the victim’s address book. Melissa’s rapid spread overwhelmed email servers worldwide, causing an estimated $80 million in damages.

Polymorphic viruses also became prominent in the 1990s. These viruses could change their code as they spread, making them harder to detect. One notable example was the Tequila virus, discovered in 1991, which could generate millions of variants of itself.
The CIH virus, also known as Chernobyl, appeared in 1998. It was particularly destructive, attempting to overwrite critical system information on infected computers. On April 26, 1999, CIH activated, causing millions of dollars in damages worldwide.
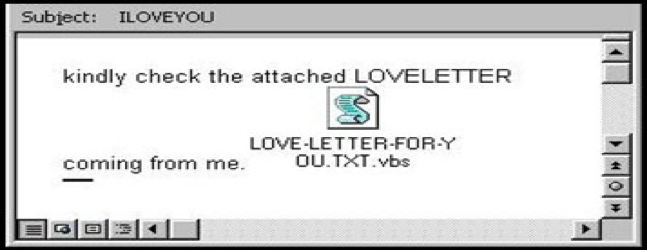
The decade concluded with the ILOVEYOU virus in 2000, which spread via email with the subject line “ILOVEYOU” and an attachment named “LOVE-LETTER-FOR-YOU.TXT.vbs”. It infected over 50 million computers in just 10 days, causing an estimated $5.5 billion in damages.
These 1990s viruses highlighted the growing sophistication of malware and the increasing vulnerability of interconnected computer systems. They spurred significant advancements in antivirus technology and raised awareness about the importance of cybersecurity.
The Diversification (2000s)
The 2000s marked a shift in the landscape of computer viruses. This period saw viruses evolve from mere digital vandalism to sophisticated tools for financial gain and espionage.
Botnets emerged as a significant threat. These networks of infected computers, controlled remotely by attackers, were used for various malicious activities. The Storm Worm, which appeared in 2007, created one of the largest known botnets. It spread through email and could be used for spam campaigns and distributed denial-of-service (DDoS) attacks.
Rootkits became more prevalent during this decade. These stealthy programs allowed attackers to maintain access to infected systems while hiding their presence. The Sony BMG rootkit scandal of 2005 brought this threat to public attention when it was discovered that music CDs were installing hidden software on customers’ computers.
Several notable outbreaks occurred during the 2000s:
– Code Red, discovered in 2001, exploited a vulnerability in Microsoft’s IIS web server. It infected over 359,000 servers in just 14 hours, causing widespread internet disruption.
– MyDoom appeared in 2004 and quickly became the fastest-spreading email worm in history. It was designed to perform DDoS attacks and create backdoors in infected systems.
– Conficker, detected in 2008, infected up to 15 million Microsoft servers. Its sophisticated design and rapid spread alarmed security experts worldwide.
These viruses demonstrated increasing complexity in their methods of propagation and concealment. They also showed a trend towards creating persistent threats that could be leveraged for ongoing criminal activities.
The diversification of viruses in this period led to the development of more comprehensive security solutions. Antivirus software began to incorporate additional features like firewalls and intrusion detection systems to combat the growing range of threats.

Modern Era (2010s-Present)
The modern era of computer viruses is characterized by increased sophistication and a wider range of targets.
State-sponsored malware became a significant concern. Stuxnet, discovered in 2010, targeted industrial control systems. It was designed to sabotage Iran’s nuclear program, demonstrating how viruses could be used as tools of cyber warfare.
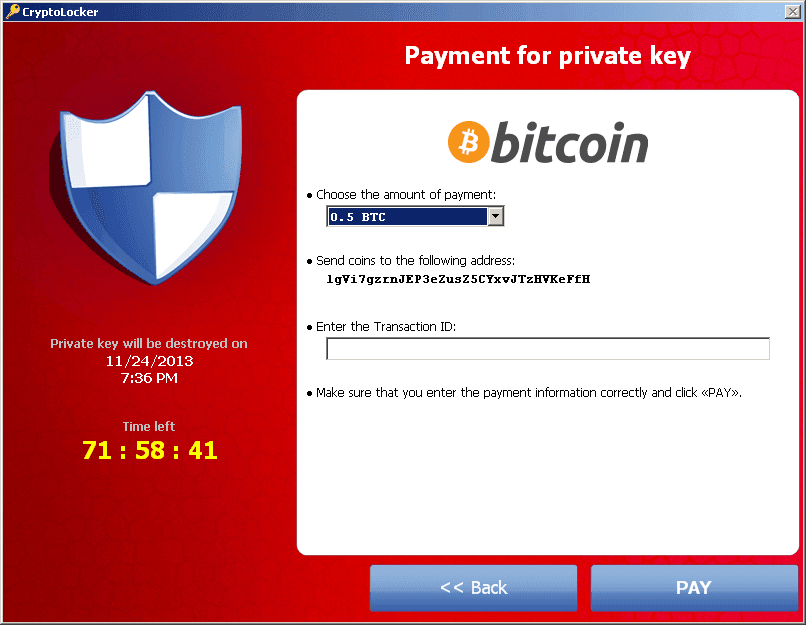
Ransomware emerged as a major threat. CryptoLocker, appearing in 2013, encrypted users’ files and demanded payment for the decryption key. This model proved lucrative for cybercriminals, leading to numerous variants.
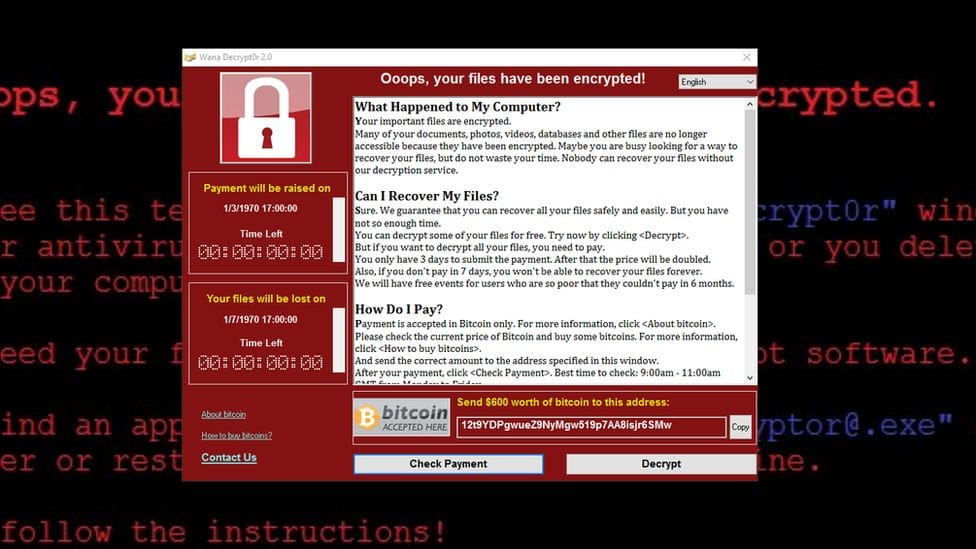
WannaCry, a ransomware attack in 2017, affected over 200,000 computers across 150 countries. It exploited a vulnerability in older Windows systems, causing widespread disruption to businesses and organizations globally.
The Internet of Things (IoT) introduced new vulnerabilities. The Mirai botnet, first seen in 2016, infected IoT devices like cameras and routers. It was used to launch massive distributed denial-of-service (DDoS) attacks, highlighting the security risks of connected devices.
Mobile devices became increasingly targeted. Android malware like FakeApp and HummingBad infected millions of devices, often through malicious apps in third-party app stores.
Artificial Intelligence (AI) started playing a role in both virus creation and defense. Machine learning algorithms were employed to create more evasive malware, while also being used to improve virus detection systems.
Cryptojacking, the unauthorized use of a computer to mine cryptocurrency, gained popularity. It often operated silently in the background, making it difficult for users to detect.
This era also saw an increase in supply chain attacks. The SolarWinds incident in 2020 compromised numerous government agencies and companies through infected software updates.
The complexity and scale of modern virus threats have led to the development of more advanced security measures, including behavioral analysis, machine learning-based detection, and integrated security platforms.
Current Landscape
The current landscape of computer viruses is characterized by increasingly sophisticated threats and evolving attack vectors.
Evasion techniques have become more advanced. Modern viruses often use polymorphic code, which changes with each infection, making them harder to detect. Some employ fileless malware techniques, residing only in system memory to avoid traditional file-based detection methods.
Cryptojacking has gained popularity among cybercriminals. This type of attack covertly uses a victim’s computing resources to mine cryptocurrency. It’s often less noticeable than other forms of malware, allowing it to persist for longer periods.
Supply chain attacks have become more prevalent. The SolarWinds incident in 2020 demonstrated how compromising a widely-used software provider can lead to widespread infections. This attack affected numerous government agencies and major corporations, highlighting the far-reaching consequences of such breaches.
Ransomware attacks have grown more targeted and damaging. Cybercriminals now often research their victims to determine how much ransom they can demand. Some groups have adopted a “double extortion” tactic, threatening to leak stolen data if the ransom isn’t paid.
The rise of remote work due to the COVID-19 pandemic has expanded the attack surface for many organizations. Home networks and personal devices often lack the robust security measures found in corporate environments, creating new vulnerabilities.
Artificial intelligence and machine learning are being used by both attackers and defenders. These technologies can create more convincing phishing attempts or generate new malware variants. Conversely, they’re also employed in advanced threat detection systems.
Mobile devices remain a significant target, with malware often disguised as legitimate apps. The increasing use of smartphones for financial transactions and multi-factor authentication makes them particularly attractive to attackers.
The threat landscape continues to change rapidly, requiring constant vigilance and adaptation from both individuals and organizations to maintain effective cybersecurity.
What You Need To Know?
Computer viruses have come a long way since their inception. From simple programs designed to replicate and spread, they’ve become complex tools capable of causing significant damage and disruption.
The progression of viruses reflects broader trends in technology and society. As our reliance on digital systems has grown, so too has the potential impact of malicious software. What began as academic experiments and relatively harmless pranks has transformed into a multi-billion dollar criminal industry and a tool for geopolitical conflict.
Key points in this evolution include:
- The shift from physical media to network-based spread
- The transition from notoriety-seeking to profit-driven motives
- The increasing sophistication of evasion and infection techniques
- The expansion of targets from personal computers to mobile devices, IoT, and industrial systems
Looking ahead, several trends are likely to shape the future of computer viruses:
- The continued integration of AI and machine learning in both attack and defense strategies
- The growing importance of supply chain security
- The challenges posed by the expanding Internet of Things
- The potential for quantum computing to disrupt current encryption methods
The ongoing battle against computer viruses underscores the importance of cybersecurity awareness and education. As threats continue to evolve, so must our approaches to protection and mitigation.
The history of computer viruses highlights the importance of ongoing research, development, and collaboration in the field of cybersecurity to safeguard our increasingly connected world.