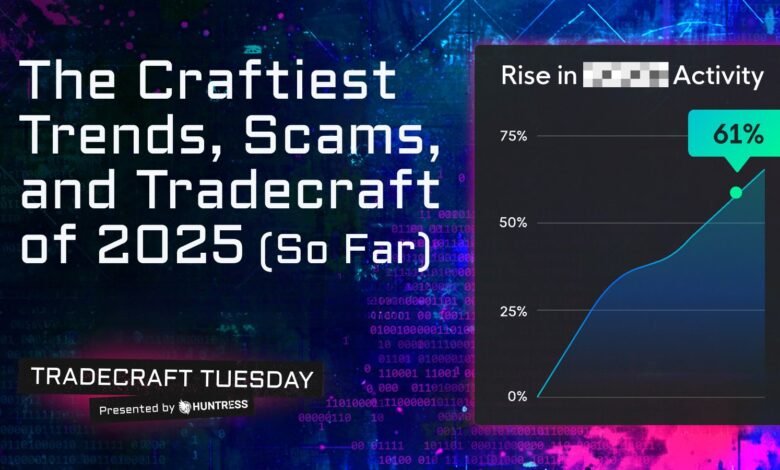
North Korean IT workers have long infiltrated Western tech firms, generating billions for their government, and have recently expanded into…
Read More »cybersecurity threats
NSO Group, the developer of Pegasus spyware, is nearing acquisition by a U.S. consortium led by Robert Simonds, pending Israeli…
Read More »Legitimate open-source tools Velociraptor and Nezha are being weaponized by threat actors to maintain access, evade detection, and deploy ransomware…
Read More »Cybercriminals are leveraging AI to create sophisticated spam, malicious code, and phishing campaigns, while also directly targeting AI systems to…
Read More »Trinity of Chaos, a ransomware collective with ties to major cybercrime groups, has launched a TOR-based data leak site listing…
Read More »XWorm malware has evolved with ransomware capabilities and over 35 plugins, distributed by multiple threat actors through phishing campaigns after…
Read More »Cybersecurity threats are intensifying due to unpatched devices and supply chain compromises, as seen in attacks on Cisco firewalls and…
Read More »North Korea's covert IT worker program has expanded beyond targeting American tech and cryptocurrency firms to now include a wide…
Read More »Approximately 48,000 Cisco ASA devices remain vulnerable to active zero-day attacks, posing ongoing risks globally, with the majority located in…
Read More »The BRICKSTORM espionage campaign targets legal, technology, SaaS, and BPO firms to steal intellectual property and sensitive data, requiring immediate…
Read More »A wave of sophisticated cyberattacks is exploiting newly discovered zero-day vulnerabilities in critical enterprise infrastructure, including Cisco's ASA and Fortra's…
Read More »Ransomware attacks have surged dramatically, with a 20% increase in victims in the first half of the year, driven by…
Read More »The Scattered Spider hacking group poses a severe threat to businesses by using sophisticated methods like social engineering and ransomware,…
Read More »A new ransomware called "Obscura," discovered in late August 2025, uses domain infrastructure to stealthily spread across corporate networks by…
Read More »Obsidian Security has launched a new defense system specifically designed to secure AI agents in SaaS environments, addressing the security…
Read More »One in three UAE companies has faced spoofing or deepfake attacks, highlighting a major shift toward sophisticated impersonation tactics as…
Read More »A decade-old security flaw known as the pixie dust attack continues to threaten networks by exploiting weaknesses in the Wi-Fi…
Read More »A self-replicating worm named Shai-Hulud has infected hundreds of open-source JavaScript packages on NPM, actively seeking credentials to spread further…
Read More »Cybersecurity leaders are grappling with AI's dual role as both a critical defense tool and a vulnerability, with widespread adoption…
Read More »Neglected assets, such as abandoned cloud instances and outdated technology, expand the attack surface by providing easy entry points for…
Read More »