ClickFix Attacks Jump 517% in 2025 – What You Need to Know
▼ Summary
– ClickFix social engineering attacks have surged by 517% in six months, becoming the second most common attack vector after phishing.
– These attacks accounted for nearly 8% of all blocked attacks in the first half of 2025, according to ESET data.
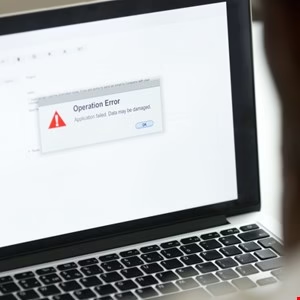
– ClickFix manipulates victims with fake error messages to copy and run malicious scripts themselves.
– The tactic exploits users’ tendency to fix issues independently, bypassing security by having victims self-infect.
– First observed in March 2024 by Proofpoint, ClickFix attacks grew rapidly by the end of that year.
Cybercriminals are increasingly exploiting human psychology through ClickFix attacks, with recent data showing a staggering 517% surge in these social engineering schemes. This alarming trend positions ClickFix as the second most prevalent threat vector, trailing only behind traditional phishing attempts. Security analysts warn that these attacks now represent nearly 8% of all blocked cyber threats during the first half of 2025.
Unlike conventional malware distribution methods, ClickFix attacks employ deceptive error messages or verification prompts to trick users into compromising their own systems. Victims are manipulated into copying and pasting malicious scripts, which they then execute themselves—often believing they’re resolving a technical issue. This self-inflicted infection method proves particularly dangerous because it bypasses many automated security measures, relying instead on human error.
The tactic capitalizes on a common behavioral tendency: when faced with what appears to be a system error, many users attempt quick fixes rather than reporting the problem to IT support. This false sense of urgency and self-reliance makes ClickFix attacks remarkably effective. Security researchers first identified the technique in early 2024, but its adoption among threat actors has grown exponentially, with a sharp uptick in incidents toward the end of that year.
Organizations are urged to prioritize employee education alongside technical defenses. Training staff to recognize suspicious prompts and report unusual system messages can significantly reduce vulnerability to these socially engineered threats. As cybercriminals refine their tactics, maintaining vigilance against evolving attack methods remains critical for both businesses and individual users.
(Source: InfoSecurity)





