Digital sovereignty is a growing global priority, leading Red Hat to release an open-source, self-assessment toolkit that helps organizations evaluate…
Read More »Linux
Entity category: technology
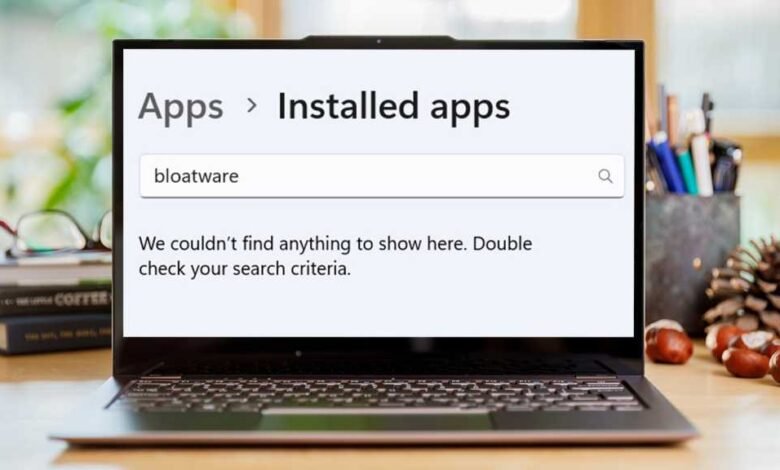
Winhance is a free, open-source tool that simplifies cleaning up unwanted pre-installed software and configuring settings on a new Windows…
Read More »Open source software is foundational to enterprise tech but creates security risks, as incidents often stem from known vulnerabilities with…
Read More »REMnux v8 is a major rebuild of the malware analysis Linux distribution, migrating to Ubuntu 24.04 and introducing a new,…
Read More »A widespread malware campaign exploits Google's trusted services, using over 4,000 malicious Google Groups and 3,500 Google-hosted URLs to distribute…
Read More »Brutus is an open-source, multi-protocol credential testing tool written in Go, designed as a single binary to streamline workflows and…
Read More »The primary alternative to Google's mobile ecosystem involves using modified versions of Android (AOSP forks) that remove proprietary services, prioritizing…
Read More »OpenVPN 2.7.0 introduces multi-socket server support for managing multiple IPs and protocols, simplifying complex network setups. The update enhances client-side…
Read More »A new malware called **'RustyRocket'**, used by the extortion group World Leaks, is designed for stealthy data theft and persistent…
Read More »The Linux 6.19 kernel is the final release in the 6.x series, delivering significant security and performance enhancements for enterprise…
Read More »The ideal Linux distribution for development depends on your specific tools, workflow, and target application platform, with several options offering…
Read More »Intel has discontinued several key open-source projects, including the Intel Graphics Compiler for Linux and the oneAPI Construction Kit, to…
Read More »Linux 7.0 has been officially released, marking a major version milestone that reflects a substantial development cycle rather than a…
Read More »A ransomware attack on SmarterTools began via an unpatched, employee-created virtual machine running outdated SmarterMail software, which allowed lateral movement…
Read More »The Linux 6.19 kernel delivers major performance gains for modern Intel and AMD CPUs through updates to core subsystems like…
Read More »AMD's next-generation RDNA 5 graphics architecture is slated to debut in a 2026 Steam Machine and then power the next…
Read More »A new, highly sophisticated ransomware-as-a-service operation named **Vect** is rapidly emerging, posing a critical threat by targeting organizations and actively…
Read More »OpenAI has launched a new macOS desktop app, Codex, which acts as a command center for orchestrating multiple AI coding…
Read More »NVIDIA has launched a native Linux client for GeForce NOW as a Flatpak, officially supporting Ubuntu 24.04 LTS and newer,…
Read More »The article highlights several indispensable, professional-grade open-source tools that are considered best-in-class, including Docker for efficient app deployment and server…
Read More »