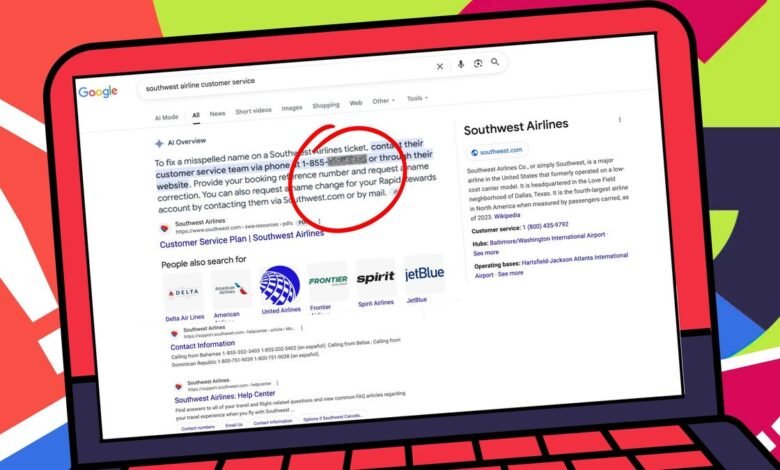
AI-powered search tools can be manipulated by scammers to display fraudulent customer service numbers, leading users to unknowingly share sensitive…
Read More »hackers
Entity category: person
Scammers are exploiting Google's AI summaries to display fake customer service numbers, tricking users into sharing personal and financial information.…
Read More »MFA blocks ~99% of automated attacks but isn't foolproof, as weak passwords can still create security gaps, requiring a layered…
Read More »Stolen credentials are cybercriminals' top tool due to their simplicity and effectiveness, bypassing the need for advanced hacking techniques. Passwords…
Read More »Outdated cybersecurity tools like legacy VPNs and web servers create vulnerabilities, becoming weak points in network defenses rather than providing…
Read More »Cyberattacks frequently target human vulnerabilities, as seen in Clorox's $380M breach caused by lax authentication practices by its IT vendor,…
Read More »Major sporting events are prime targets for cybercriminals due to their global attention and financial stakes, leading to sophisticated attacks…
Read More »Smartphones are prime targets for cybercriminals and surveillance due to their sensitive data, with tools like Stingrays mimicking cell towers…
Read More »Files encrypted with the .rgPrGzyZY extension indicate a severe ransomware attack, locking data until a ransom is paid, though experts…
Read More »Critical vulnerabilities in SinoTrack GPS tracking systems (CVE-2025-5484, CVE-2025-5485) could let hackers monitor vehicle locations or disable functions like fuel…
Read More »WestJet is investigating a cybersecurity breach that disrupted its website and mobile app, though flight operations remain unaffected. The airline…
Read More »AI-powered cryptocurrency bots are vulnerable to memory manipulation attacks, allowing hackers to hijack transactions and redirect funds using simple text…
Read More »